Introduction
This integration guide outlines the best-practice configuration when onboarding and operating Axis devices in HPE Aruba Networking networks. The configuration uses modern security standards and protocols such as IEEE 802.1X, IEEE 802.1AR, IEEE 802.1AE, and HTTPS.
Establishing proper automation for network integration can save you time and money. It removes unnecessary system complexity when using Axis device management applications with HPE Aruba Networking infrastructure and applications. When combining Axis devices and software with a HPE Aruba Networking infrastructure you can benefit in these ways:
Removing device staging networks minimizes system complexity.
Adding automating onboarding processes and device management reduces costs.
Axis devices provide zero-touch network security controls.
Increased overall network security through HPE and Axis expertise.
For a smooth software-defined transition between logical networks throughout the on-boarding process, the network infrastructure must be prepared to securely verify the integrity of the Axis devices before starting the configuration. You need the following before doing the configuration:
Experience of managing enterprise network IT-infrastructure from HPE Aruba Networking, including HPE Aruba Networking access switches and HPE Aruba Networking ClearPass Policy Manager.
Expertise in modern network access control techniques and network security policies.
Previous basic knowledge about Axis products is desirable, but this is also provided throughout the guide.
Secure onboarding - IEEE 802.1AR/802.1X
Initial authentication
When the Axis Edge Vault-supported Axis device is connected to the network, it uses the IEEE 802.1AR Axis device ID certificate through the IEEE 802.1X network access control to authenticate itself.
To grant access to the network, ClearPass Policy Manager verifies the Axis device ID together with other device-specific fingerprints. This information, such as the MAC-address and the device’s AXIS OS version, is used to make a policy-based decision.
The Axis device authenticates itself on the network using the IEEE 802.1AR compliant Axis device ID certificate.
- Axis device ID
- IEEE 802.1x EAP-TLS network authentication
- Access switch (authenticator)
- ClearPass Policy Manager
Provisioning
After authentication, the Axis device moves onto the provisioning network (VLAN201). This network contains AXIS Device Manager, which performs device configuration, security hardening, and AXIS OS updates. To complete the device provisioning, new customer-specific production-grade certificates are uploaded to the device for IEEE 802.1X and HTTPS.
- Access switch
- Provisioning network
- ClearPass Policy Manager
- Device management application
Production network
The provisioning of the Axis device with new IEEE 802.1X certificates triggers a new authentication attempt. ClearPass Policy Manager verifies the new certificates and decides whether or not to move the Axis device into the production network.
- Axis device ID
- IEEE 802.1x EAP-TLS network authentication
- Access switch (authenticator)
- ClearPass Policy Manager
After re-authentication, the Axis device moves into the production network (VLAN 202), where the Video Management System (VMS) connects to the device and starts operation.
- Access switch
- Production network
- ClearPass Policy Manager
- Video management system
Configuration HPE Aruba Networking
HPE Aruba Networking ClearPass Policy Manager
ClearPass Policy Manager provides role- and device-based secure network access control for IoT, BYOD, corporate devices, employees, contractors and guests, across multivendor wired, wireless, and VPN infrastructure.
Trusted certificate store configuration
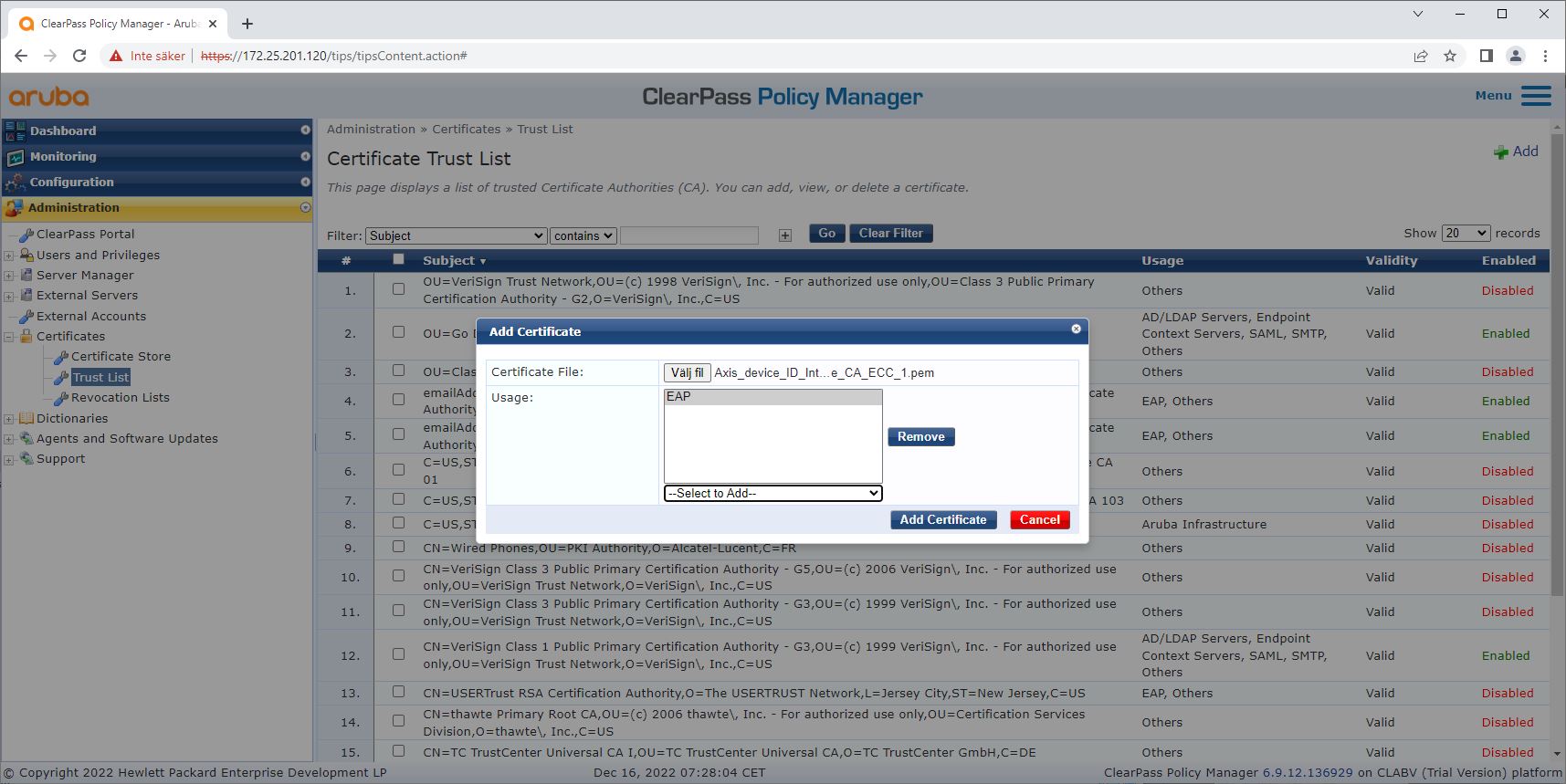
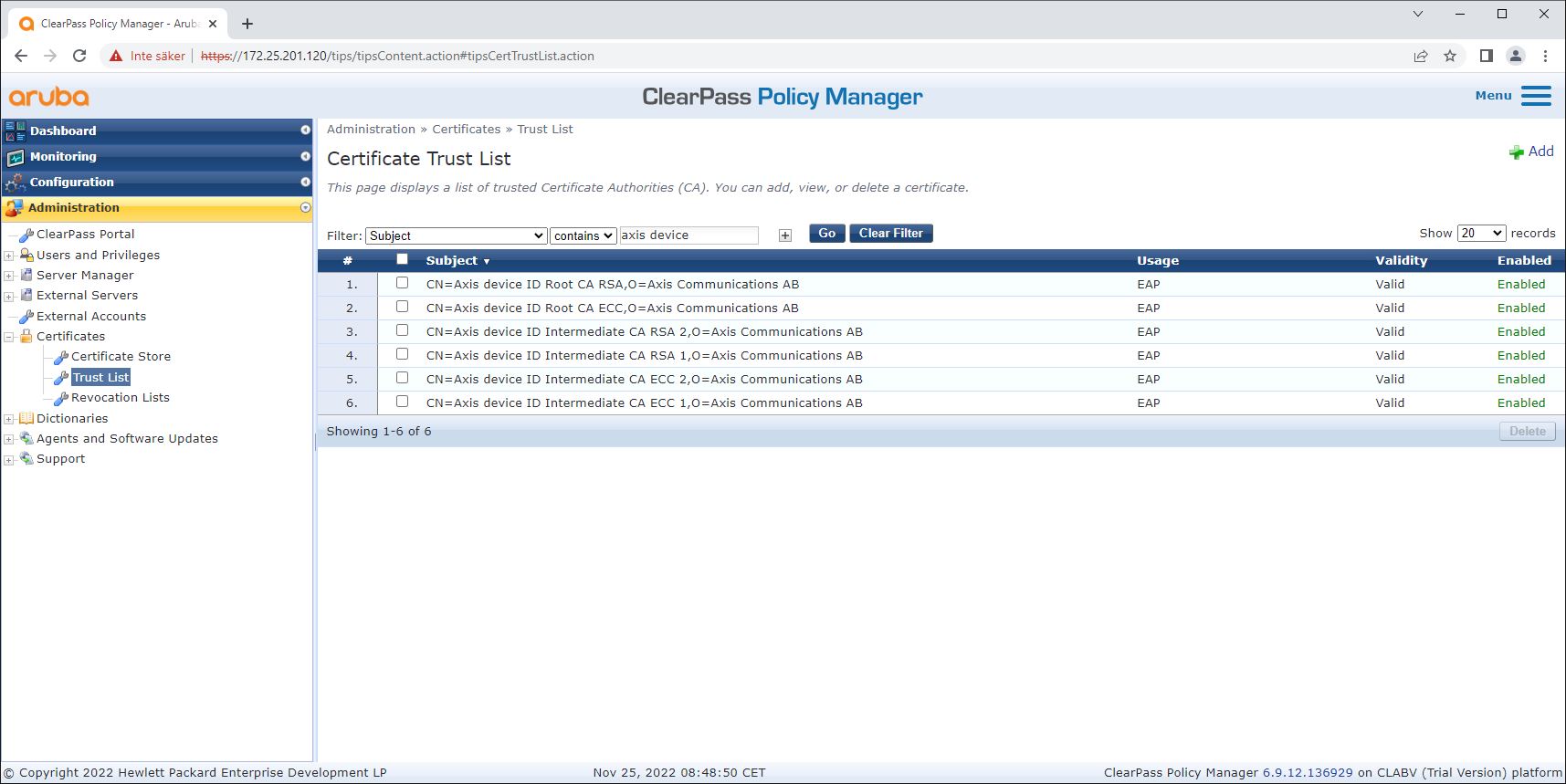
Download the Axis-specific IEEE 802.1AR certificate chain from axis.com.
Upload the Axis-specific IEEE 802.1AR Root CA and Intermediate CA certificate chains into the trusted certificate store.
Enable ClearPass Policy Manager to authenticate Axis devices through IEEE 802.1X EAP-TLS.
Select EAP in the usage field. The certificates are used for IEEE 802.1X EAP-TLS authentication.
Network device/group configuration
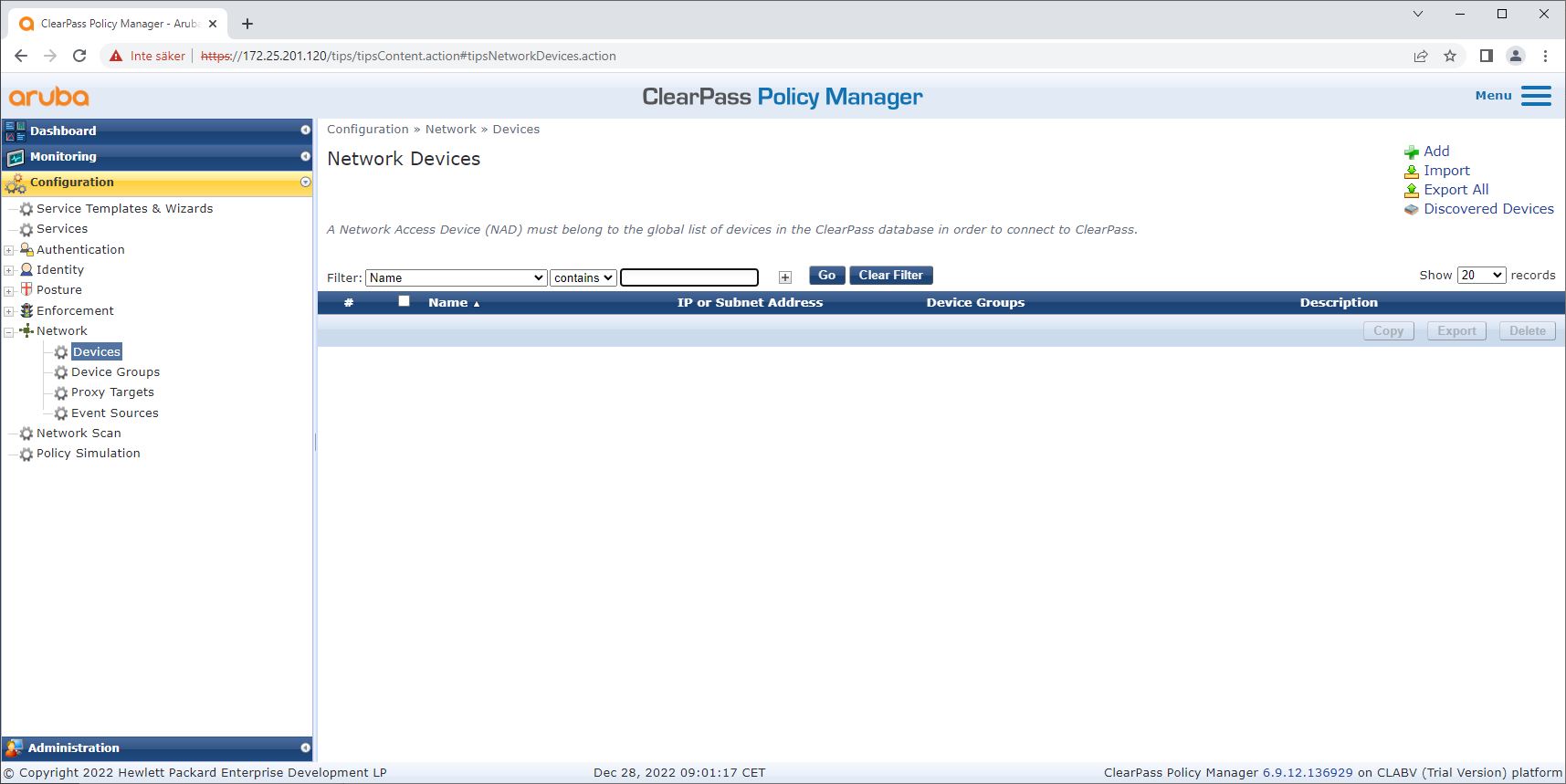
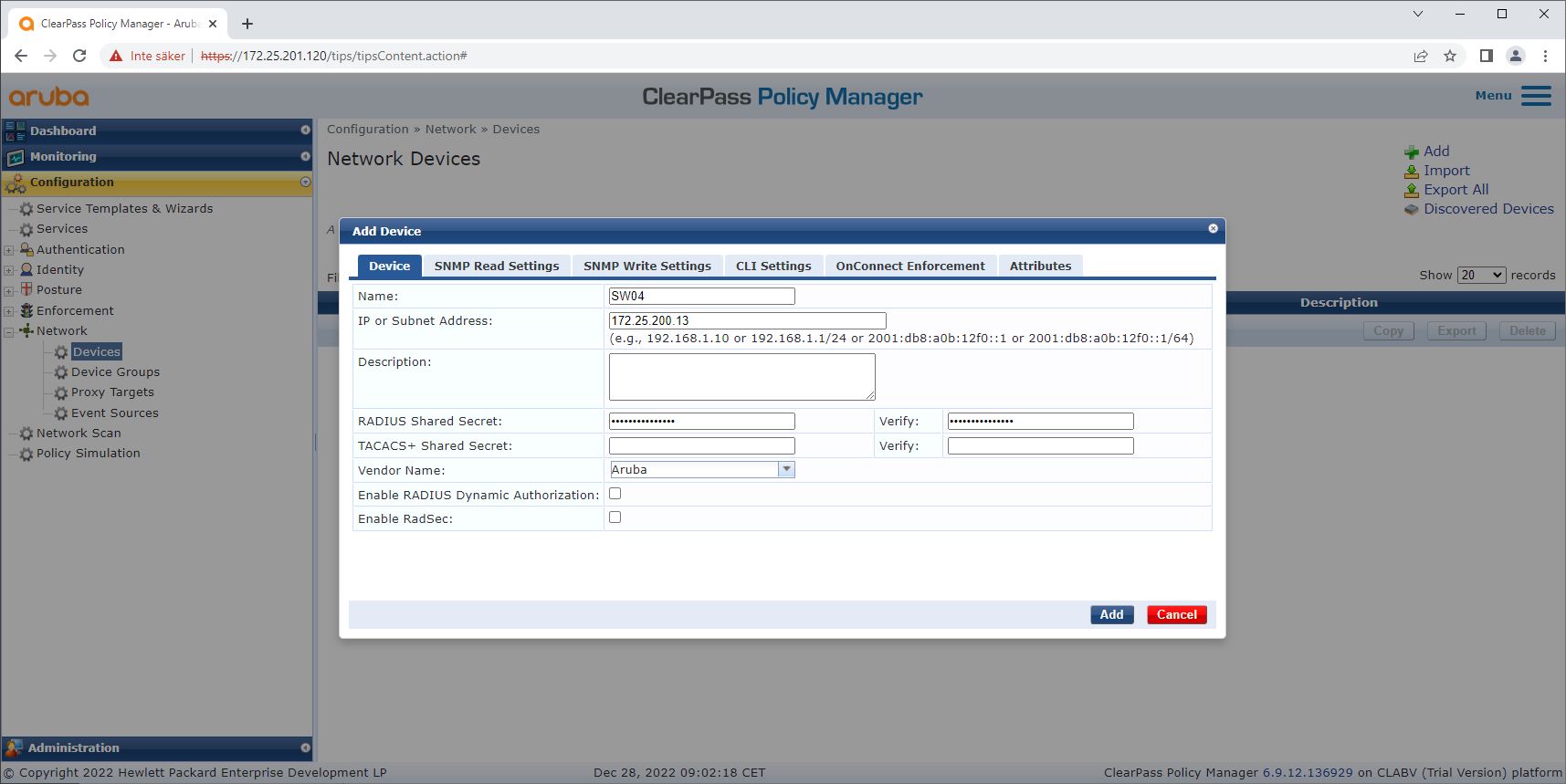
Add trusted network access devices such as HPE Aruba Networking access switches to ClearPass Policy Manager. ClearPass Policy Manager needs to know which access switches in the network are used for IEEE 802.1X communication. Note also that the RADIUS shared secret must match the specific switch IEEE 802.1X configuration
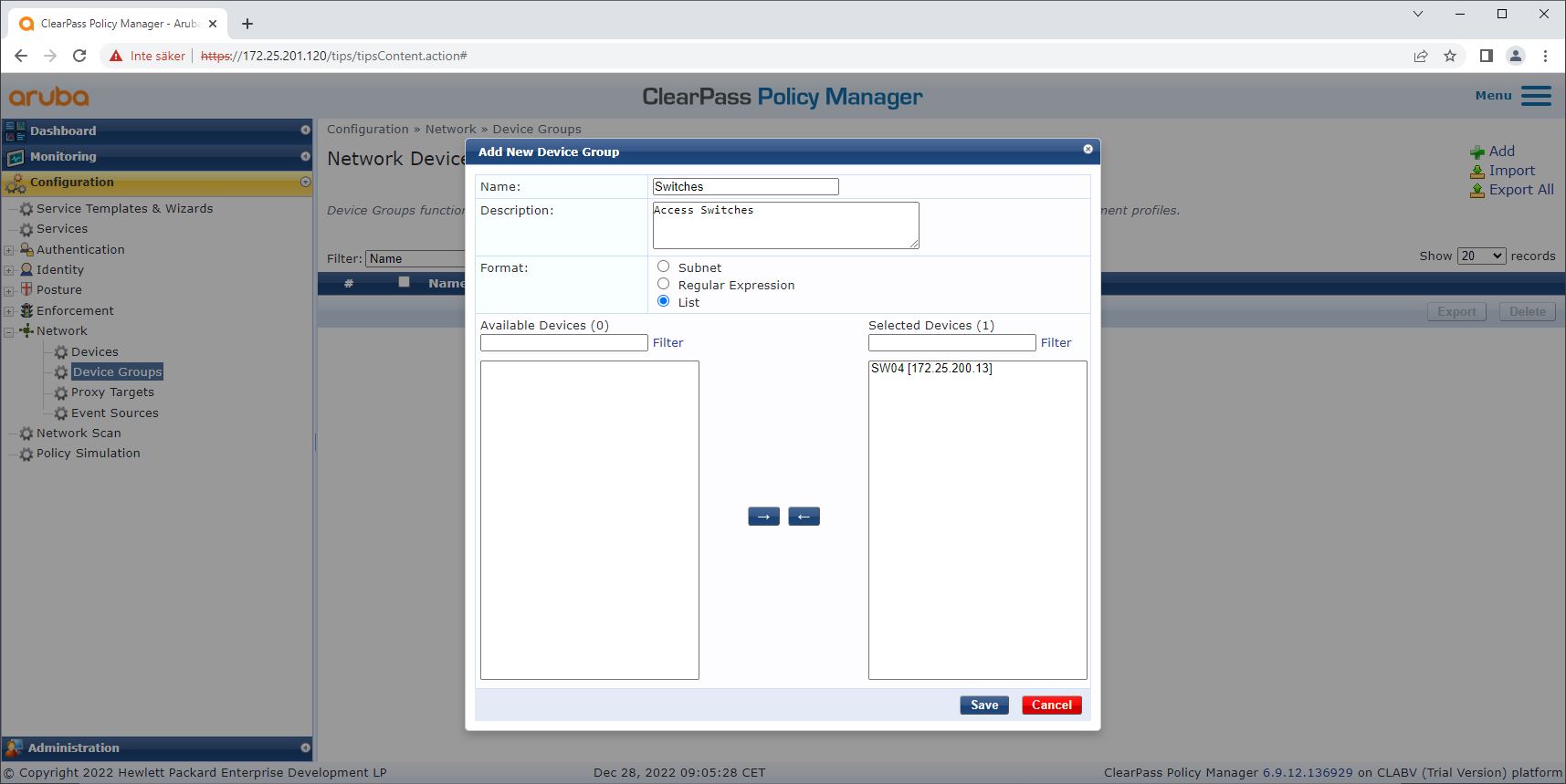
Use the network device group configuration to group multiple trusted network access devices. Grouping devices makes policy configuration easier.
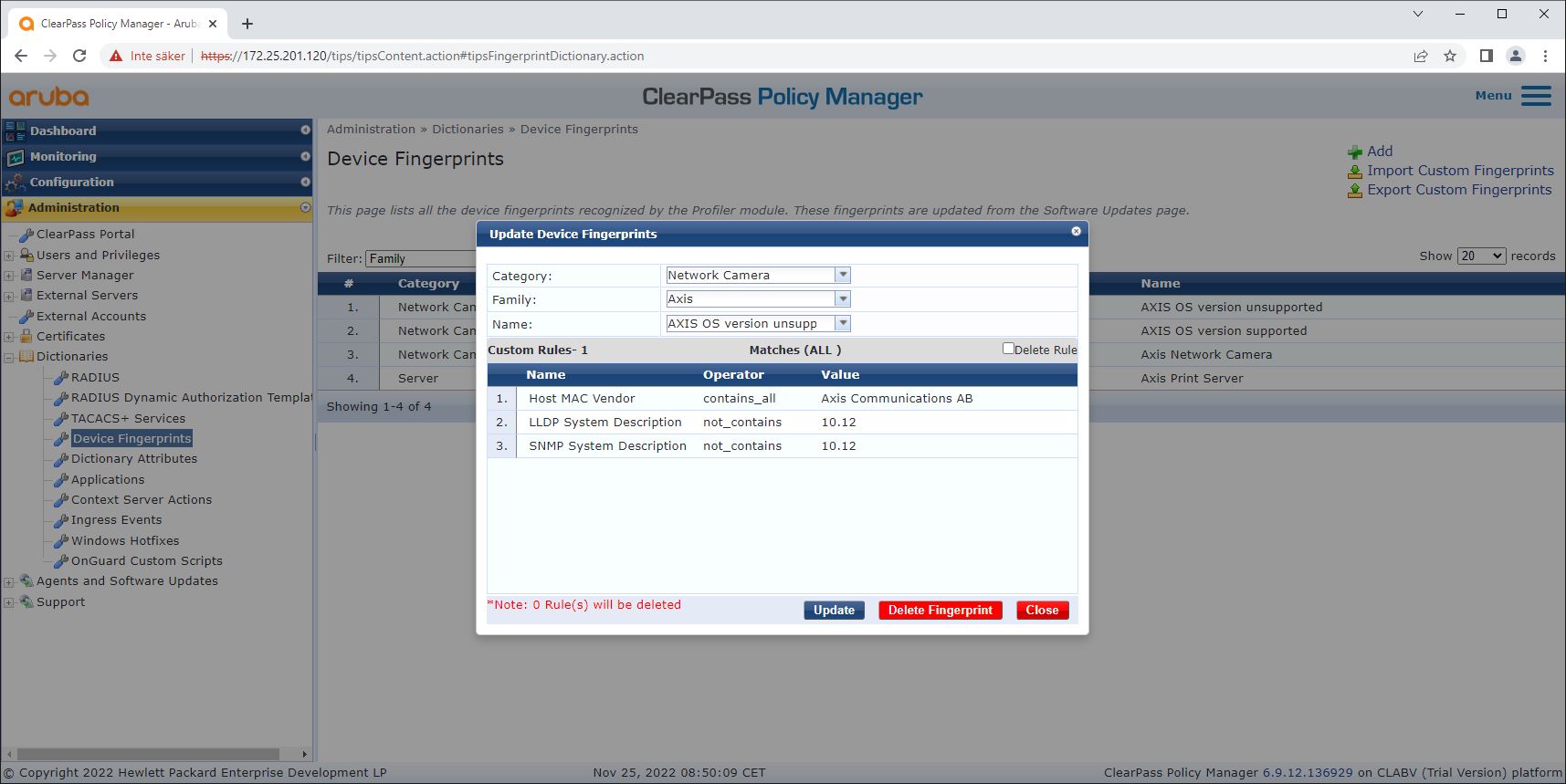
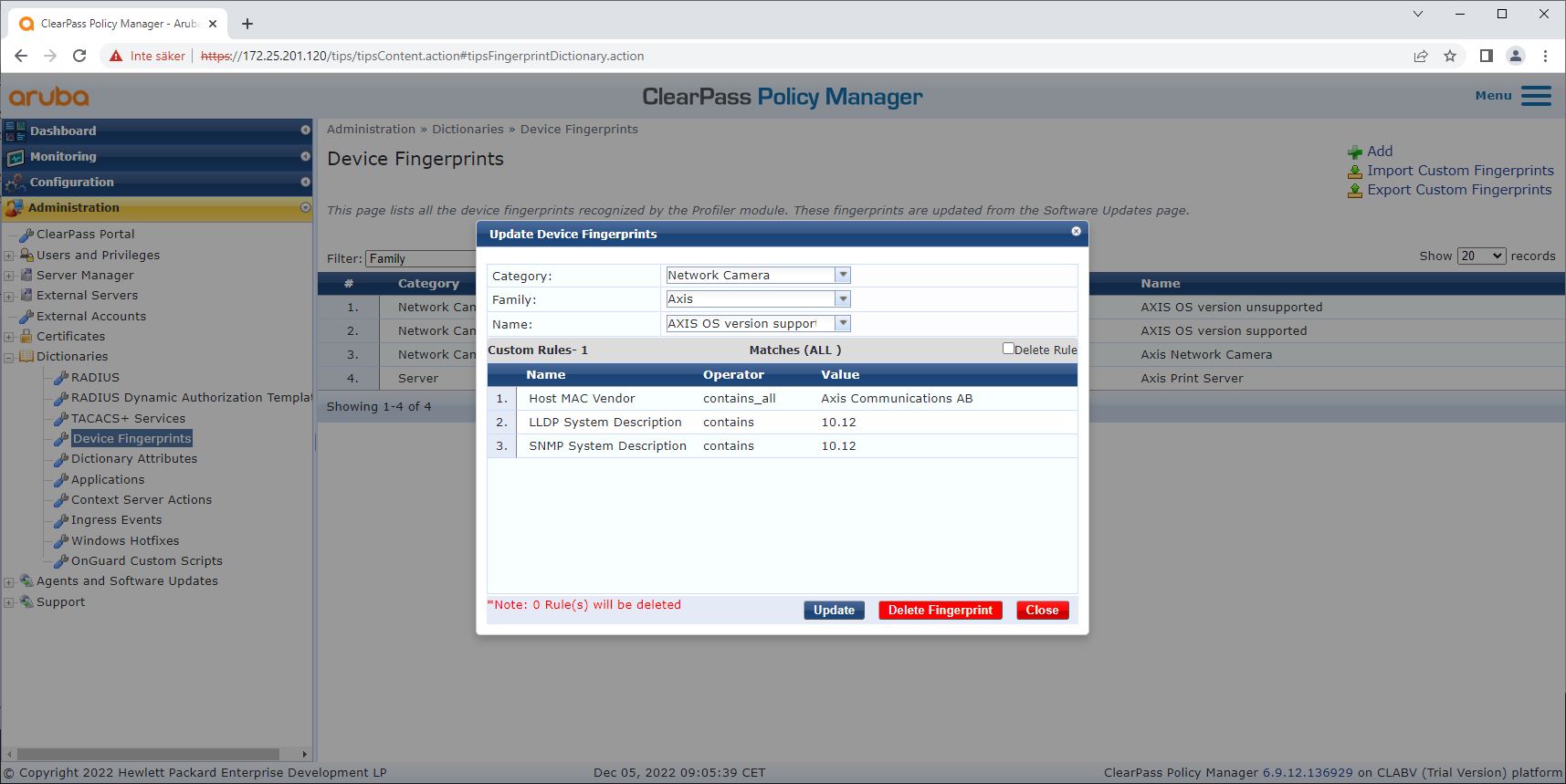
Device fingerprint configuration
The Axis device can, through network discovery, distribute device-specific information such as the MAC-address and the device software version. You can use this information to create, update, or manage a device fingerprint in ClearPass Policy Manager. You can also grant or deny access based on the AXIS OS version.
Go to Administration > Dictionaries > Device Fingerprints.
Select an existing device fingerprint or create a new device fingerprint.
Make the device fingerprint settings.
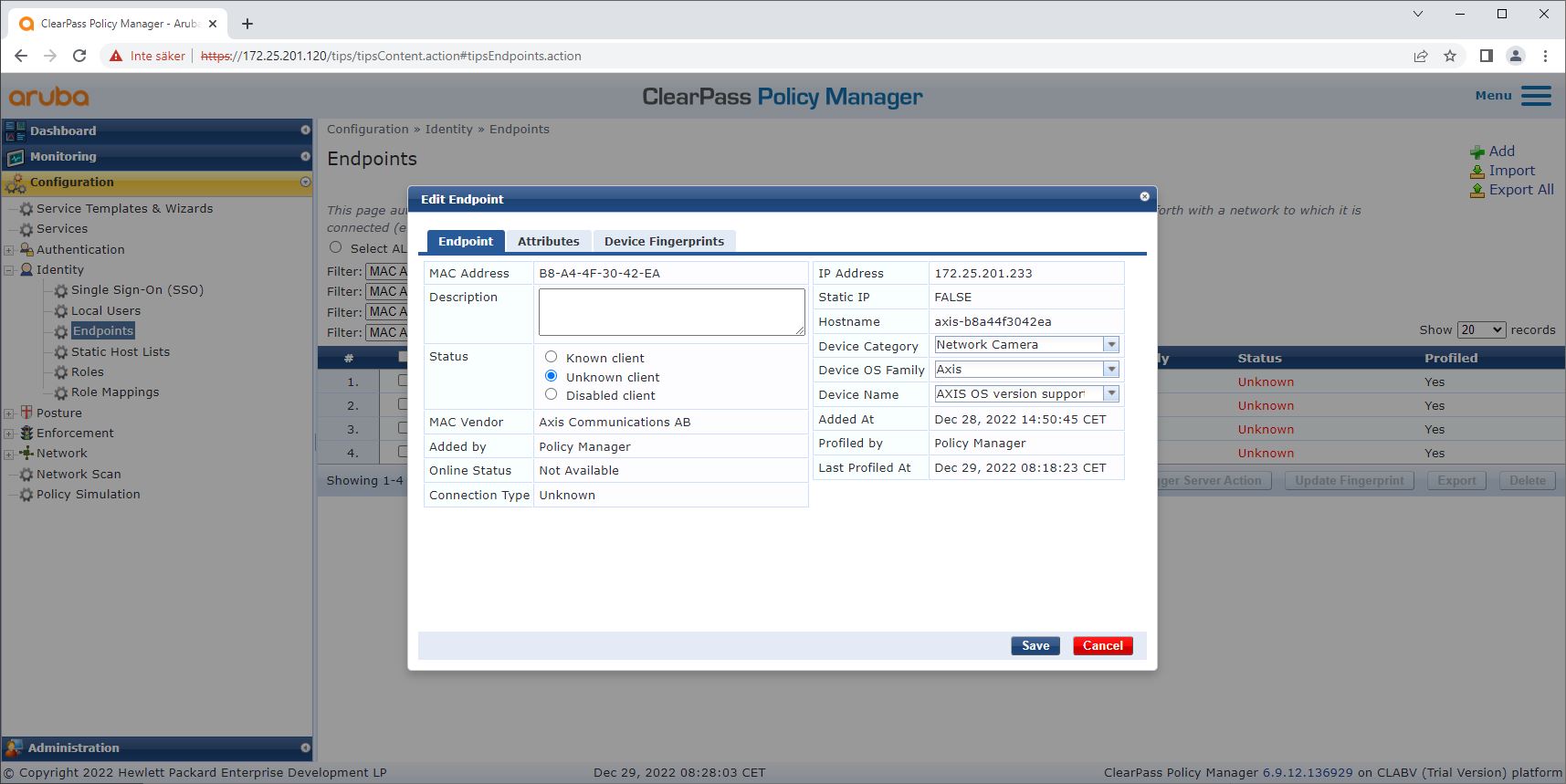
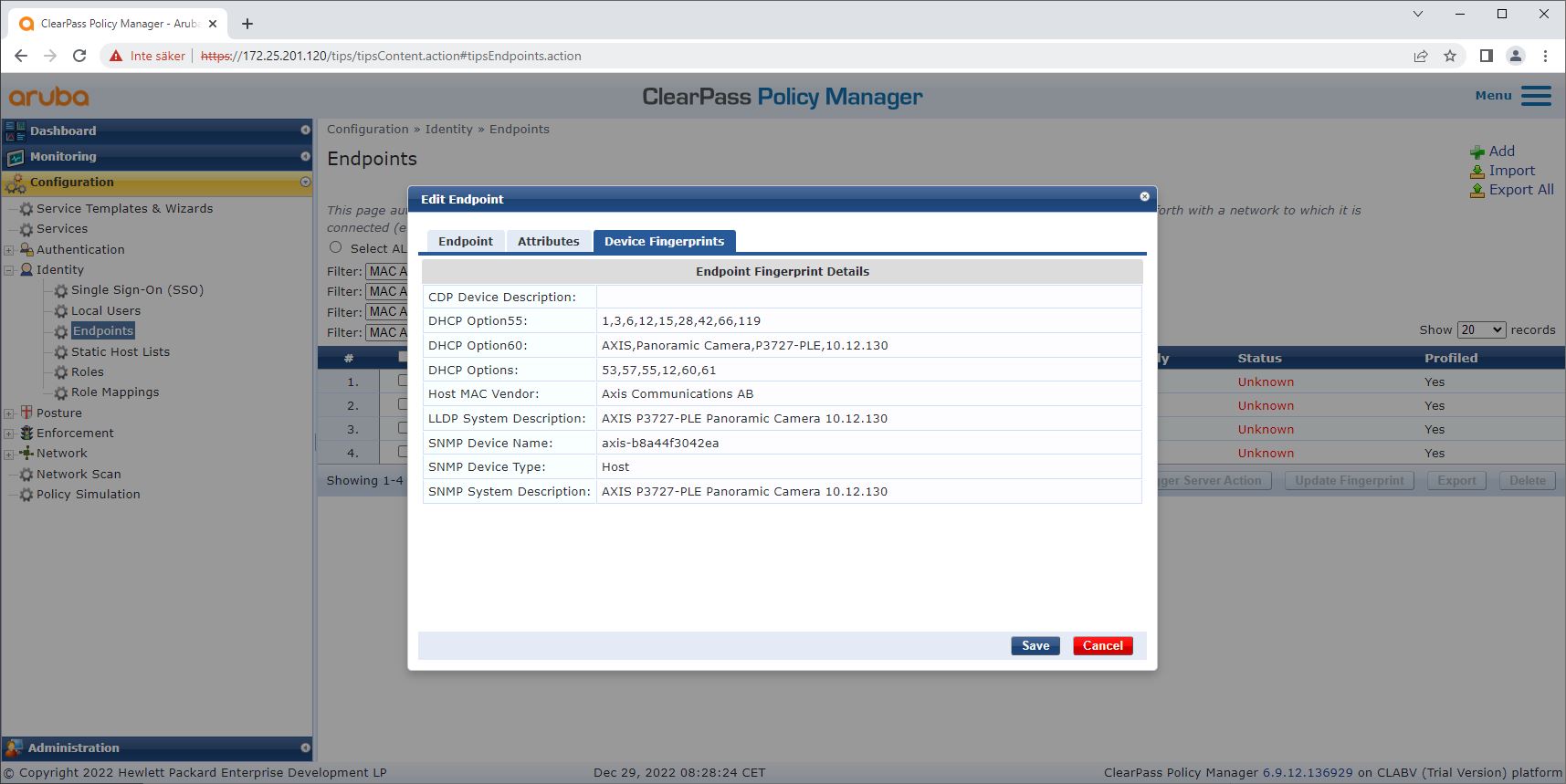
Information about the device fingerprint collected by ClearPass Policy Manager can be found in the Endpoints section.
Go to Configuration > Identity > Endpoints.
Select the device you want to view.
Click on the Device Fingerprints tab.
SNMP is disabled by default in Axis devices and collected from the HPE Aruba Networking access switch.
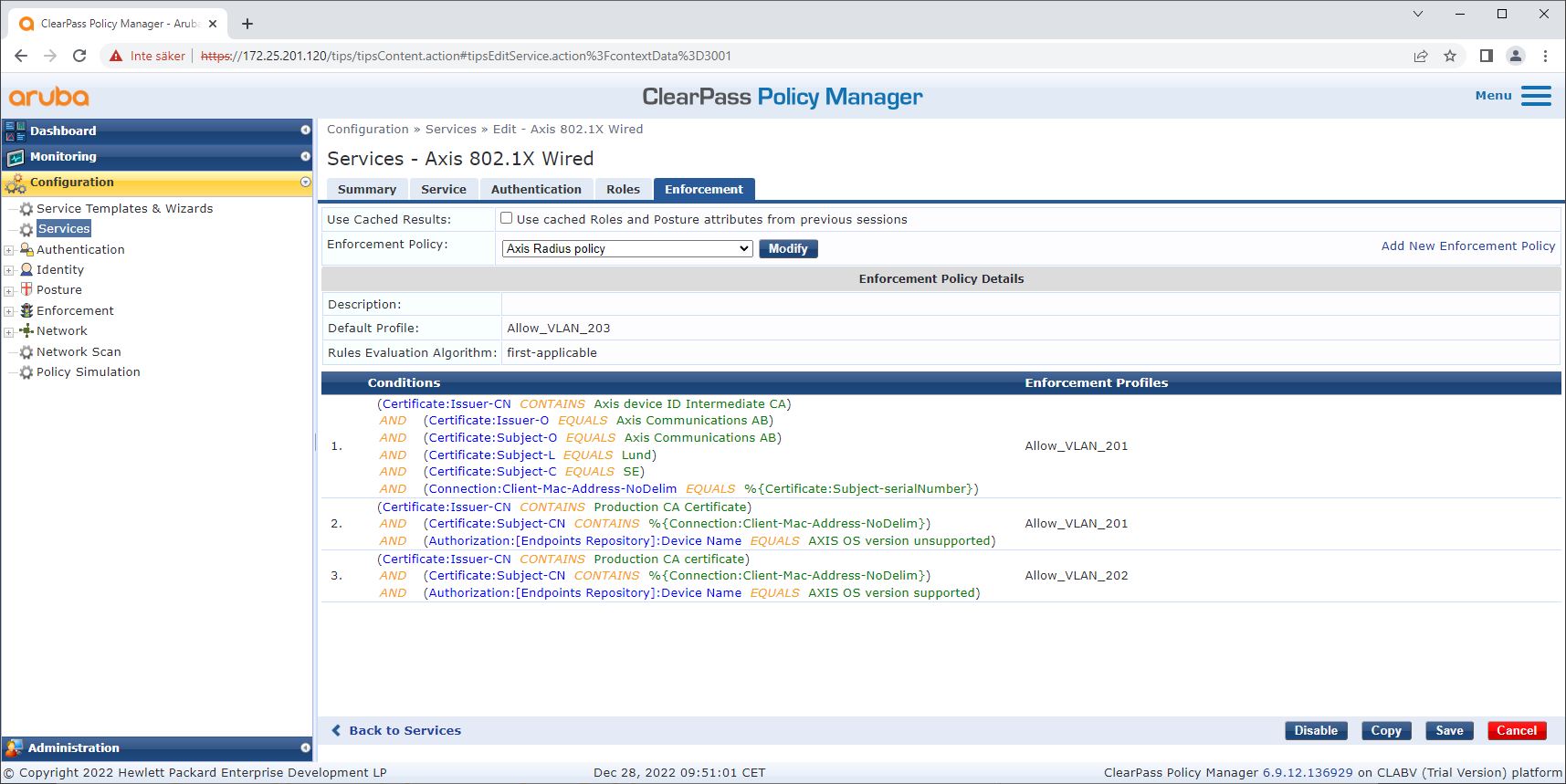
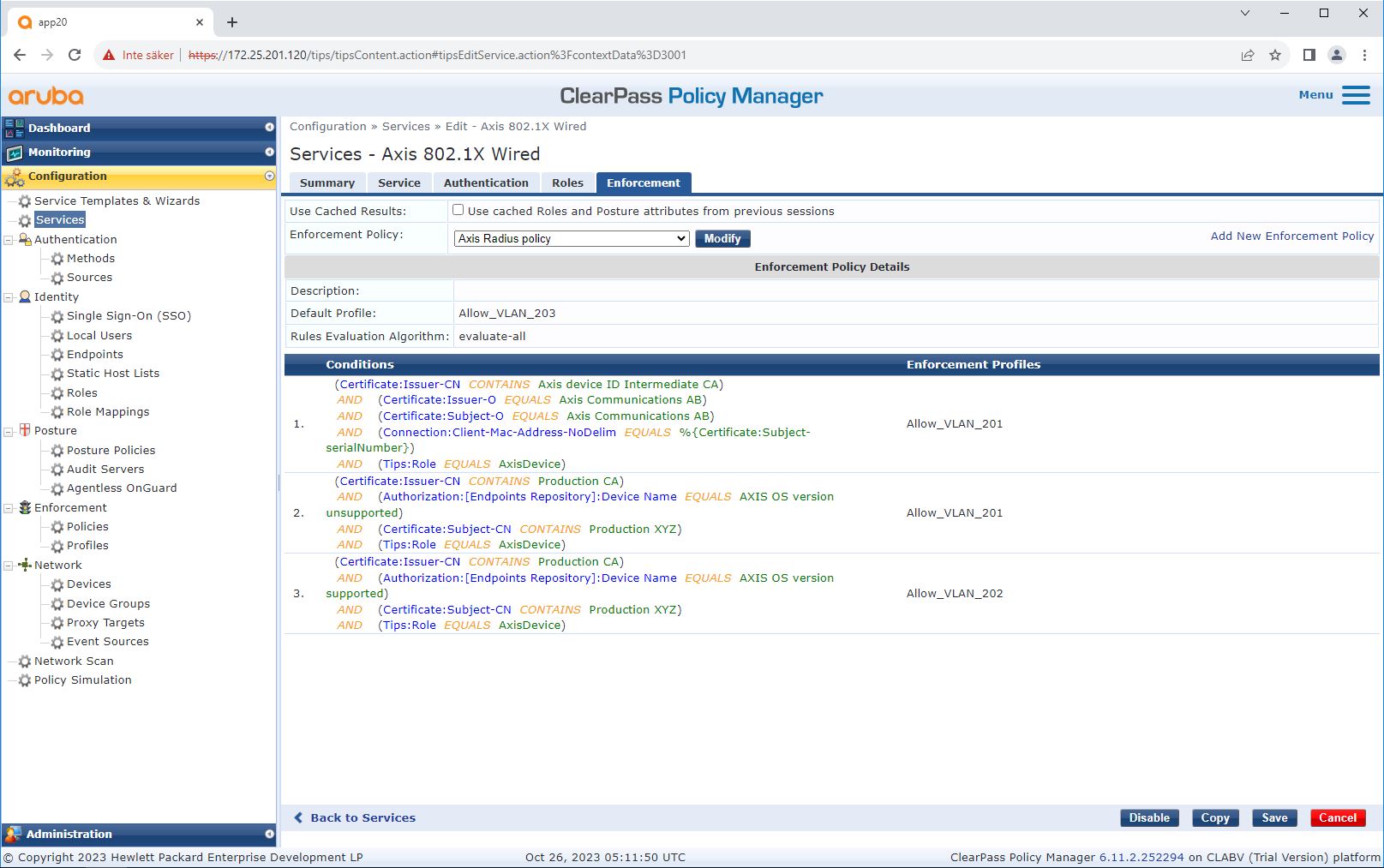
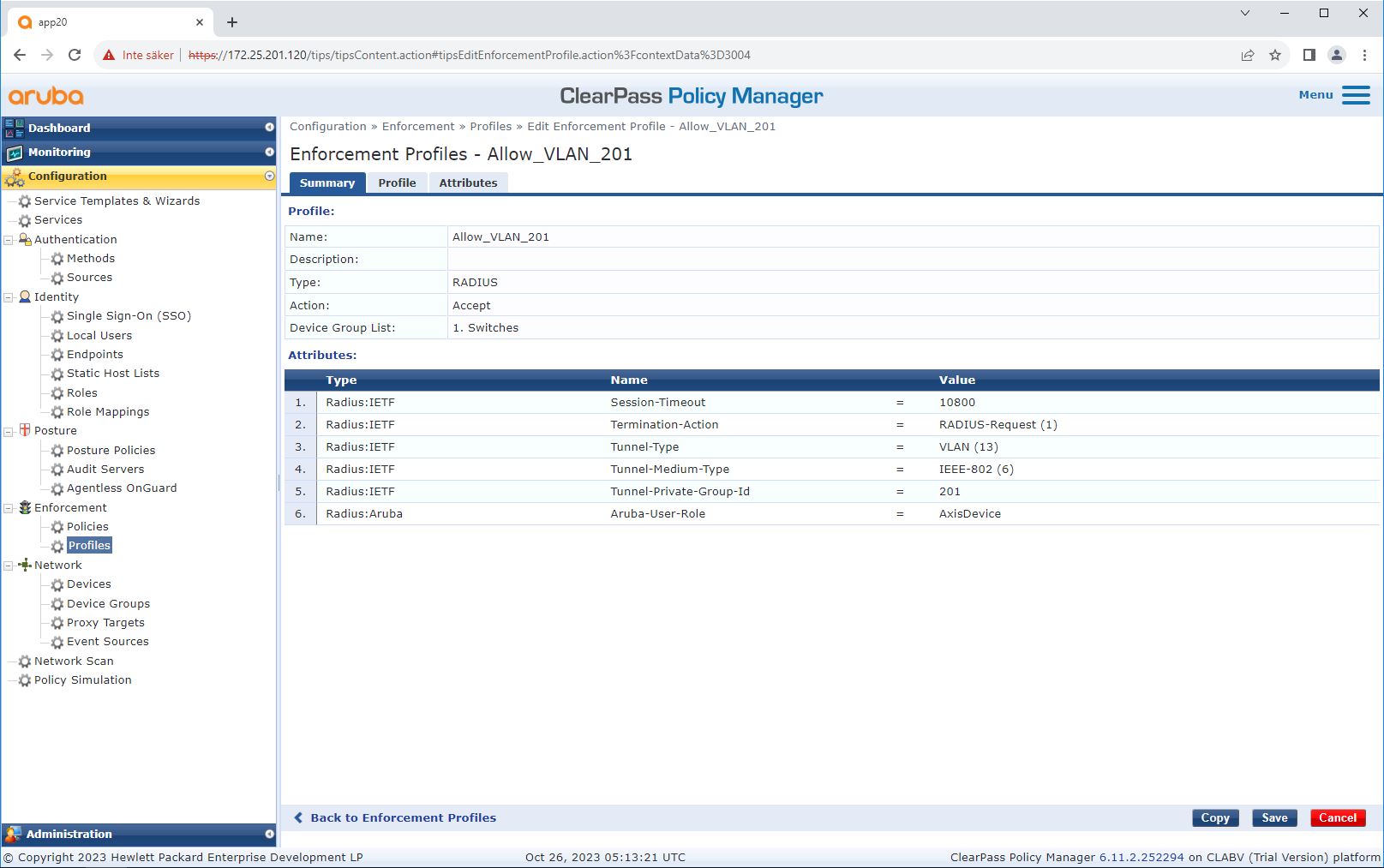
Enforcement profile configuration
Enforcement Profile allows ClearPass Policy Manager to assign a specific VLAN ID to an access port on the switch. This is a policy-based decision that applies to the network devices in the device group “Switches”. The required number of enforcement profiles depends on the number of VLANs in use. Our setup has three VLANs (VLAN 201, 202, 203), which correlate to three enforcement profiles.
After the enforcement profiles for the VLAN are configured, the enforcement policy itself can be configured. The enforcement policy configuration in ClearPass Policy Manager defines if Axis devices are granted access to HPE Aruba Networking networks based on four example policy profiles.
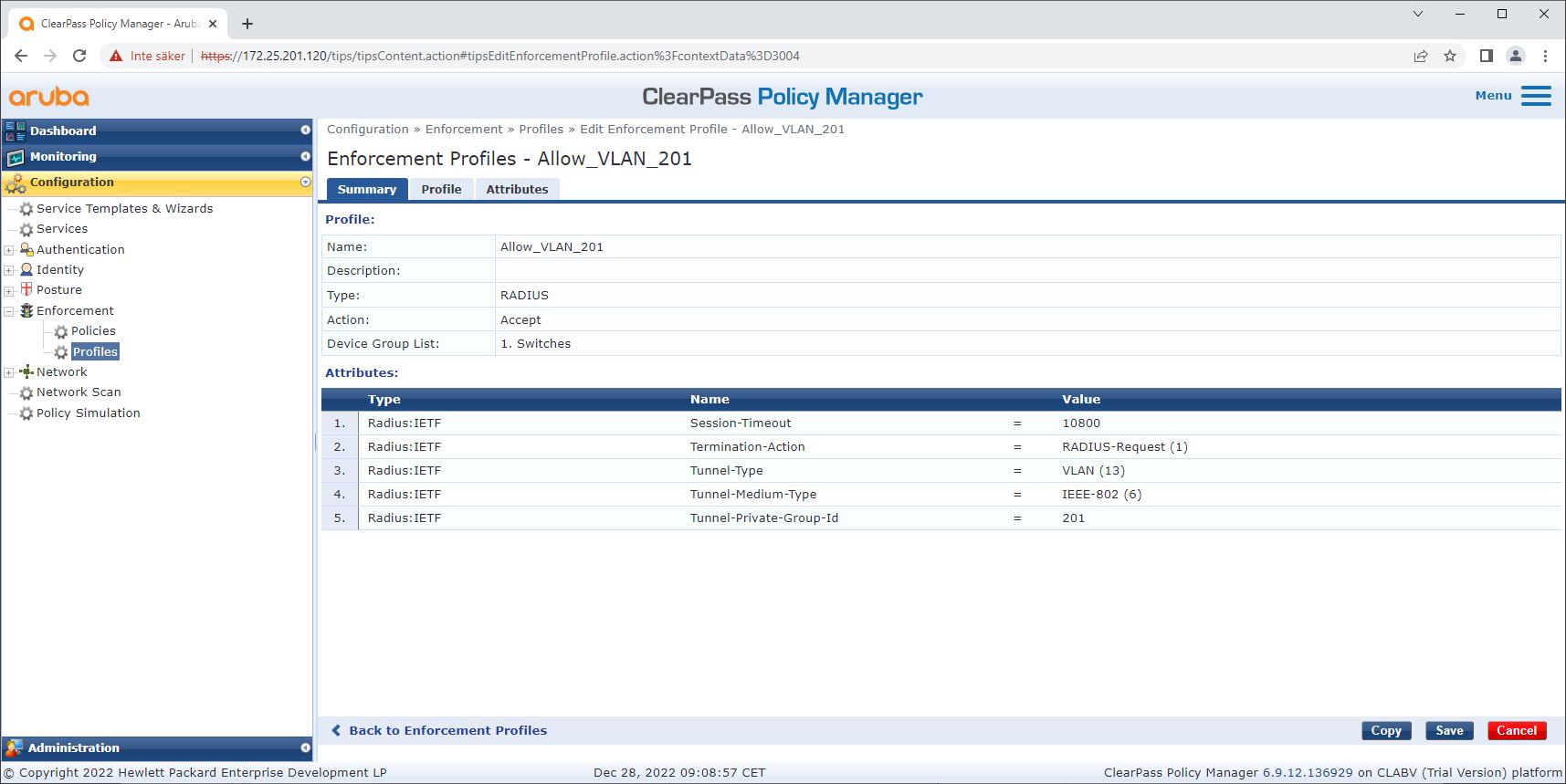
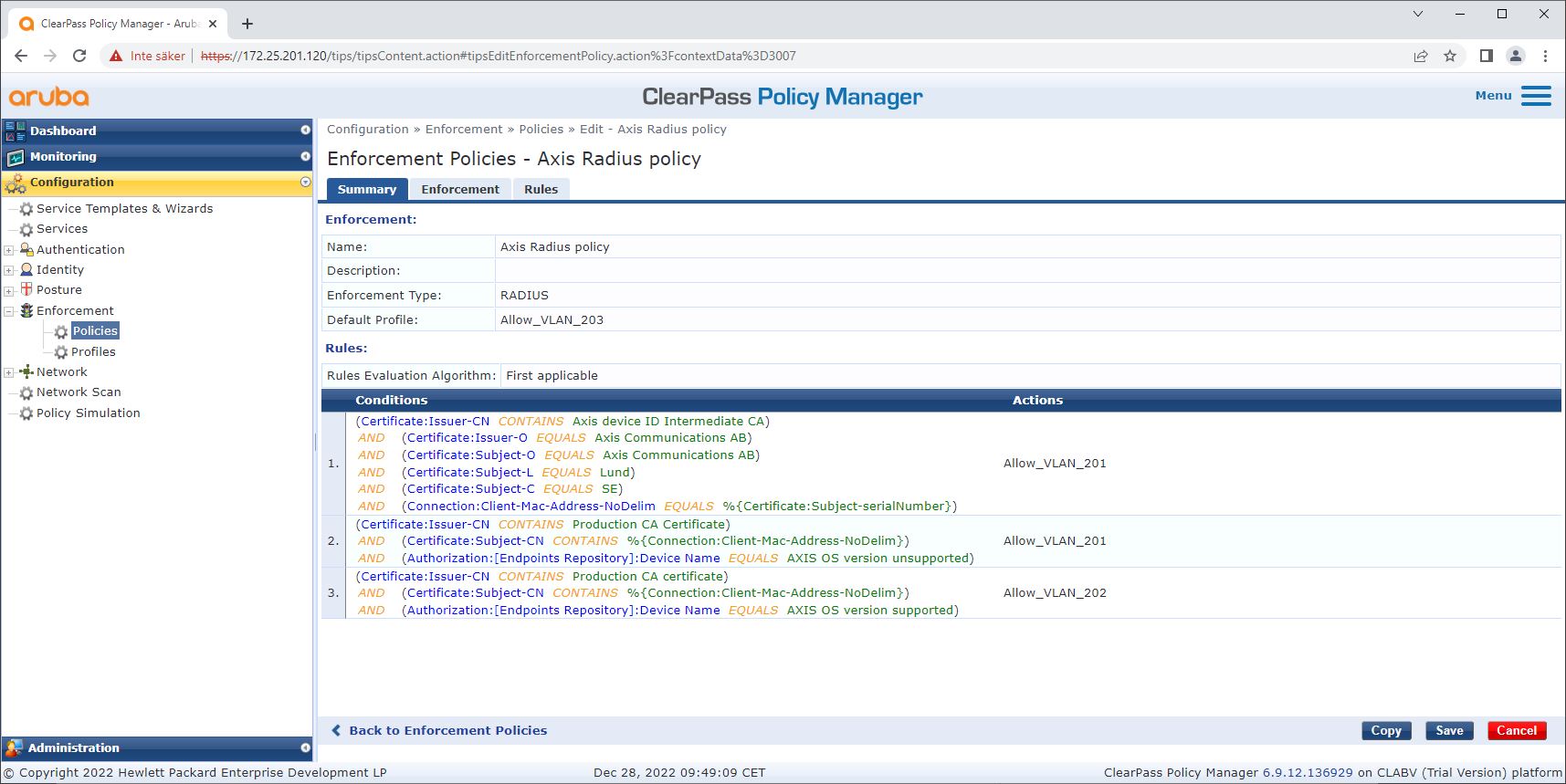
The four enforcement policies and their actions are:
Denied network access
Access to the network is denied when IEEE 802.1X network access control authentication is not performed.
Guest-network (VLAN 203)
The Axis device is granted access to a limited, isolated network if the IEEE 802.1X network access control authentication fails. Manual inspection of the device is then required, to decide on the appropriate actions.
Provisioning network (VLAN 201)
The Axis device is granted access to a provisioning network. This is to provide Axis device management capabilities through AXIS Device Manager and AXIS Device Manager Extend. It also makes it possible to configure Axis devices with AXIS OS updates, production-grade certificates, and other configurations. The following conditions are verified by ClearPass Policy Manager:
The device’s AXIS OS version.
The device’s MAC-address matches the vendor-specific MAC-address scheme, with the serial number attribute of the Axis device ID certificate.
The Axis device ID certificate is verifiable and matches the Axis-specific attributes such as issuer, organization, location, and country.
Production network (VLAN 202)
The Axis device is granted access to the production network in which it will operate. Access is granted after device provisioning is completed from within the provisioning network (VLAN 201). The following conditions are verified by ClearPass Policy Manager:
The device’s AXIS OS version.
The device’s MAC-address matches the vendor-specific MAC-address scheme, with the serial number attribute of the Axis device ID certificate.
The production-grade certificate is verifiable by the trusted certificate store.
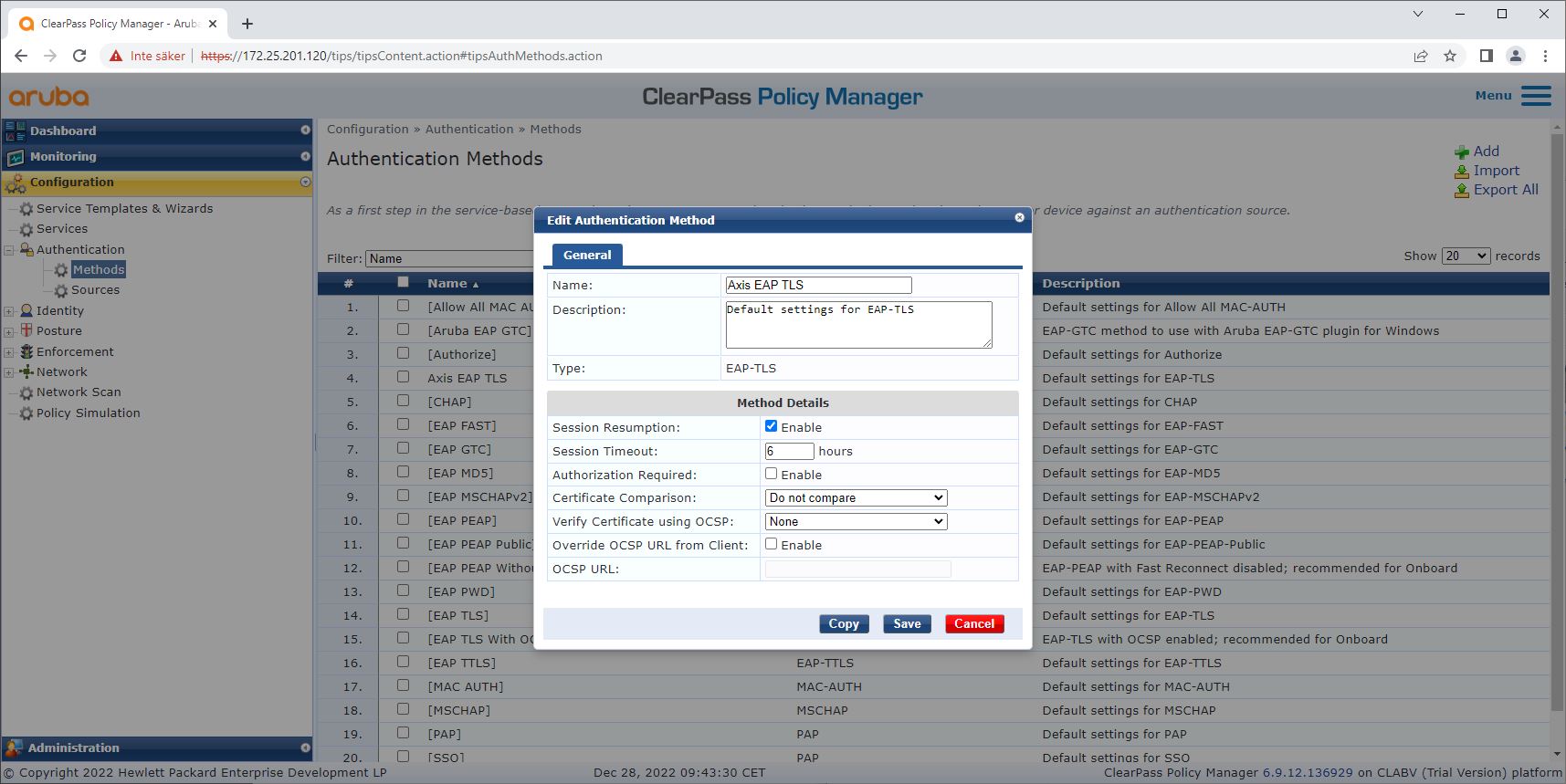
Authentication method configuration
The authentication method defines how an Axis device attempts to authenticate itself on the network. The preferred method is IEEE 802.1X EAP-TLS, as Axis devices with Axis Edge Vault come with IEEE 802.1X EAP-TLS enabled by default.
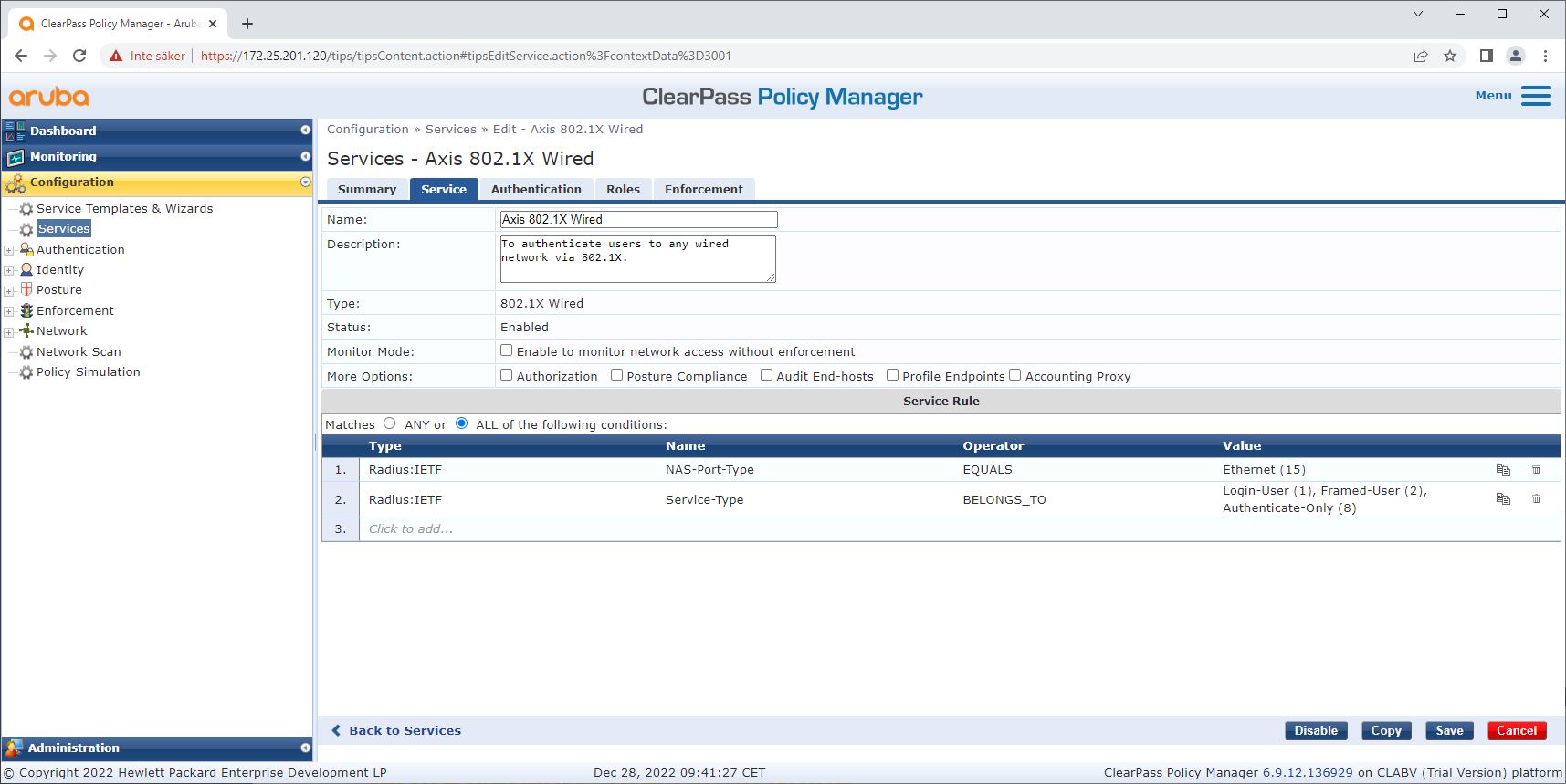
Service configuration
On the Services page, the configuration steps are combined into a single service that handles the authentication and authorization of Axis devices in HPE Aruba Networking networks.
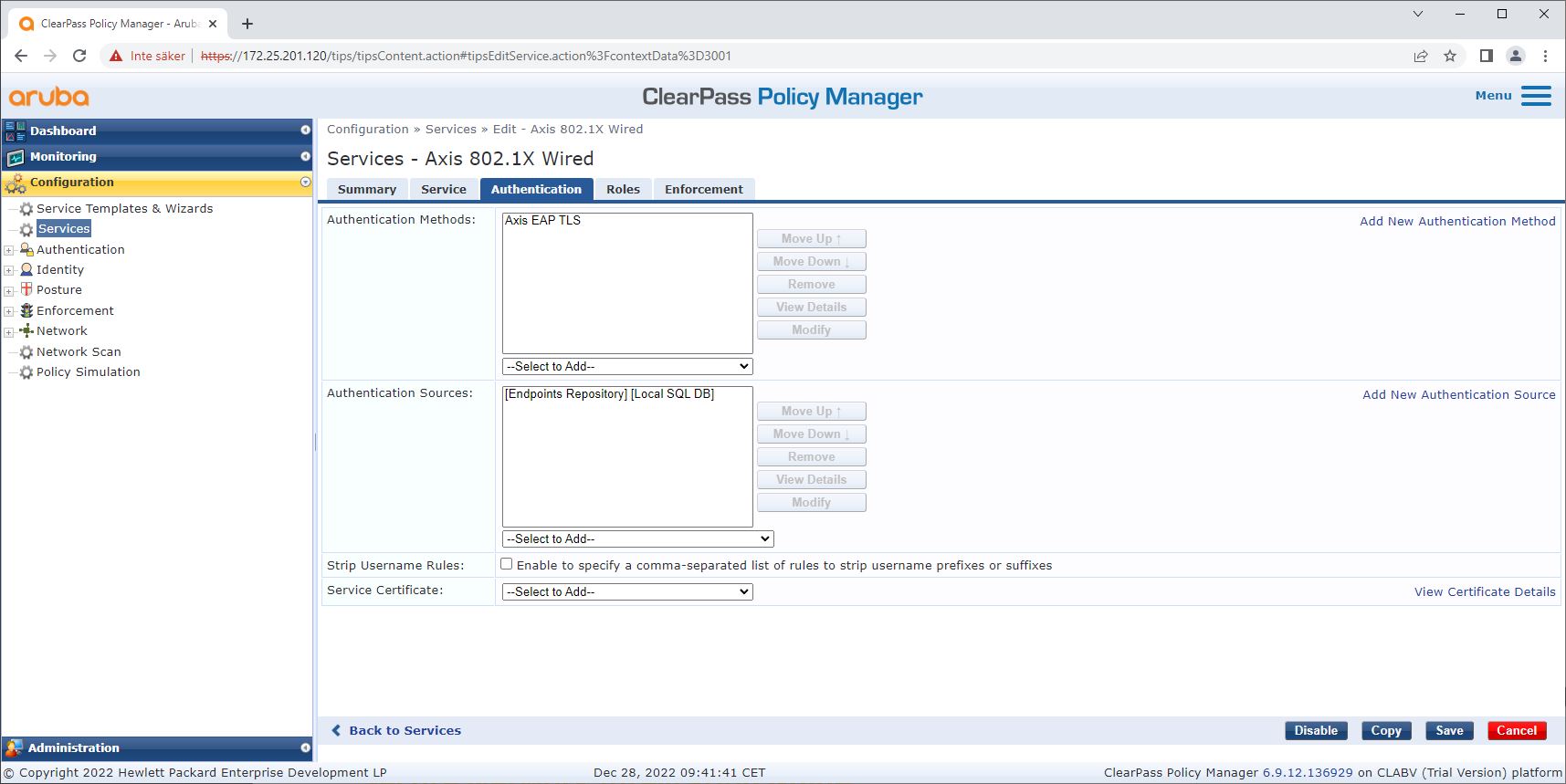
HPE Aruba Networking access switch
Axis devices are either connected directly to PoE-capable access switches, or via compatible Axis PoE midspans. To securely onboard Axis devices into HPE Aruba Networking networks, the access switch must be configured for IEEE 802.1X communication. The Axis device relays IEEE 802.1x EAP-TLS communication to ClearPass Policy Manager, which acts as a RADIUS server.
A periodic re-authentication of 300 seconds for the Axis device is also configured, to increase overall port access security.
This example shows global and port configuration for HPE Aruba Networking access switches.
radius-server host MyRADIUSIPAddress key "MyRADIUSKey"aaa authentication port-access eap-radius
aaa port-access authenticator 18-19
aaa port-access authenticator 18 reauth-period 300
aaa port-access authenticator 19 reauth-period 300
aaa port-access authenticator activeConfiguration Axis
Axis network device
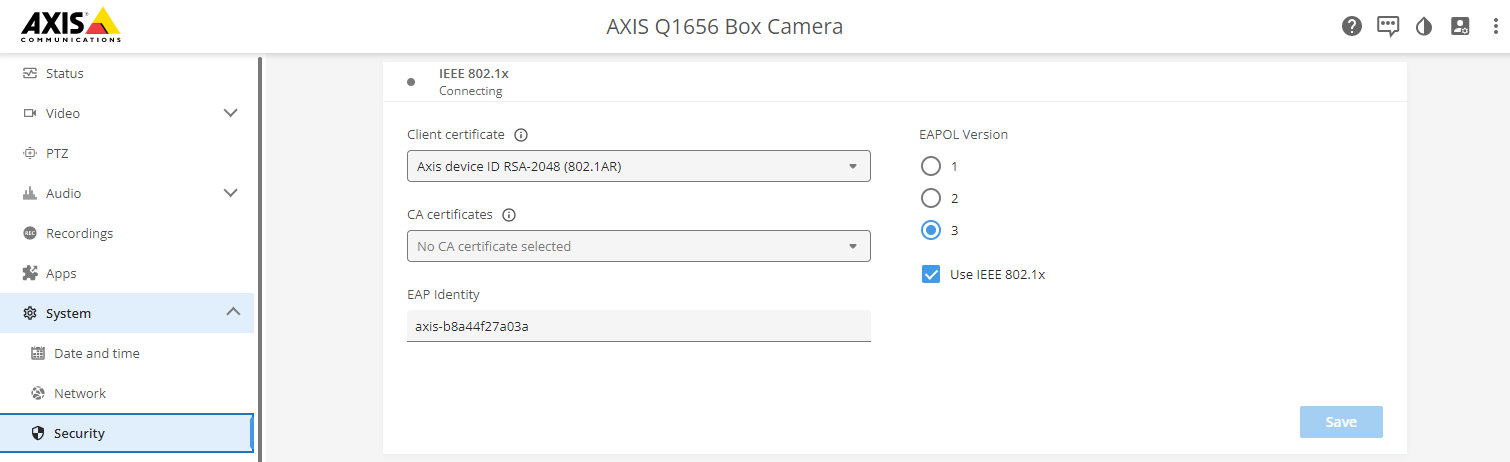
Axis devices with support for Axis Edge Vault are manufactured with a secure device identity called Axis device ID. The Axis device ID is based on the international IEEE 802.1AR standard, which defines a method for automated, secure device identification and network onboarding through IEEE 802.1X.
- Axis device ID key infrastructure (PKI)
- Axis device ID
The hardware-protected secure keystore provided by a secure element of the Axis device is factory-provisioned with a device-unique certificate and corresponding keys (Axis device ID), which can globally prove the authenticity of the Axis device. Axis Product Selector can be used to find which Axis devices have support for Axis Edge Vault and Axis device ID.
The serial number of an Axis device is its MAC-address.
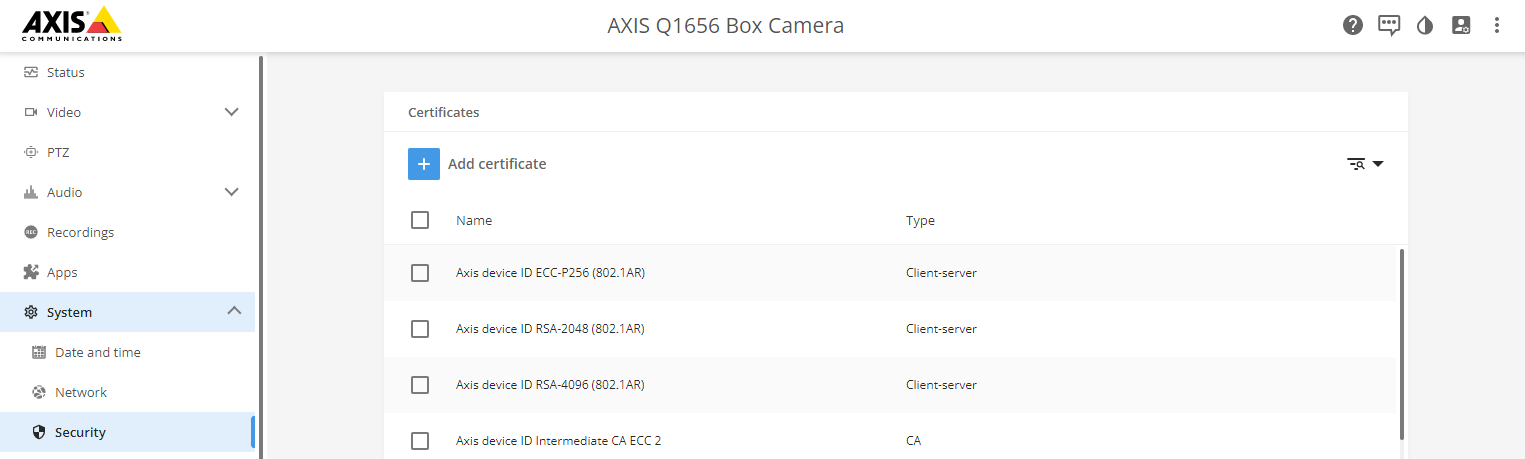
The IEEE 802.1AR-compliant Axis device ID certificate includes information about the serial number and other vendor-specific information. This information is used by ClearPass Policy Manager for analysis and decision making to grant access to the network. The information below can be obtained from an Axis device ID certificate
| Country | SE |
| Location | Lund |
| Issuer Organization | Axis Communications AB |
| Issuer Common Name | Axis device ID intermediate |
| Organization | Axis Communications AB |
| Common Name | axis-b8a44f279511-eccp256-1 |
| Serial Number | b8a44f279511 |
The common name is constructed from a combination of the Axis company name, the device’s serial number, followed by the crypto algorithm (ECC P256, RSA 2048, RSA 4096). As of AXIS OS 10.1 (2020-09), IEEE 802.1X is enabled by default with the Axis device ID pre-configured. This enables the device to authenticate itself on IEEE 802.1X-enabled networks.
AXIS Device Manager
AXIS Device Manager and AXIS Device Manager Extend can be used on the network to configure and manage multiple Axis devices in a cost-effective manner. AXIS Device Manager is a Microsoft Windows®-based application that is installed locally on a machine in the network, while AXIS Device Manager Extend relies on cloud infrastructure to perform multi-site device management. Both offer easy management and configuration capabilities, such as:
Installation of AXIS OS updates.
Application of cybersecurity configurations such as HTTPS and IEEE 802.1X certificates.
Configuration of device-specific settings, such as images settings and others.
Secure network operation - IEEE 802.1AE MACsec
IEEE 802.1AE MACsec (Media Access Control Security) is a well-defined network protocol that cryptographically secures point-to-point Ethernet links on network layer 2. It ensures the confidentiality and integrity of data transmissions between two hosts.
The IEEE 802.1AE MACsec standard describes two modes of operation:
Manually configurable Pre-Shared Key/Static CAK mode
Automatic Master Session/Dynamic CAK mode using IEEE 802.1X EAP-TLS
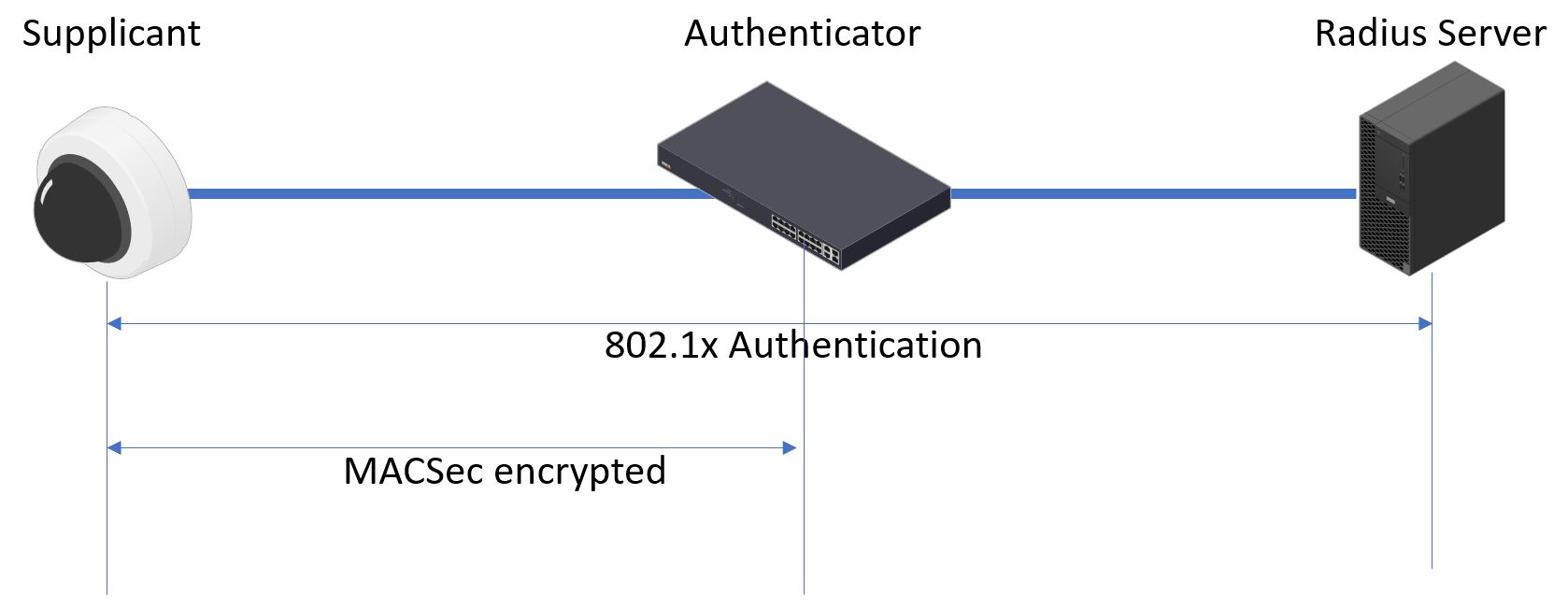
In AXIS OS 10.1 (2020-09) and later, IEEE 802.1X is enabled by default for devices that are compatible with Axis device ID. In AXIS OS 11.8 and later, we support MACsec with automatic dynamic mode using IEEE 802.1X EAP-TLS enabled by default. When you connect an Axis device with factory default values, IEEE 802.1X network authentication is performed, and when successful, MACsec Dynamic CAK mode is tried as well.
The securely stored Axis device ID (1) – an IEEE 802.1AR-compliant secure device identity – is used to authenticate on the network (4, 5) through IEEE 802.1X EAP-TLS port-based network access control (2). Through the EAP-TLS session, MACsec keys are exchanged automatically to set up a secure link (3), protecting all network traffic from the Axis device to the HPE Aruba Networking access switch.
IEEE 802.1AE MACsec requires both HPE Aruba Networking access switch and ClearPass Policy Manager configuration preparations. No configuration is required on the Axis device to allow IEEE 802.1AE MACsec encrypted communication via EAP-TLS.
If the HPE Aruba Networking access switch doesn’t support MACsec using EAP-TLS, then the Pre-Shared Key mode can be used and manually configured.
HPE Aruba Networking ClearPass Policy Manager
Role and role mapping policy
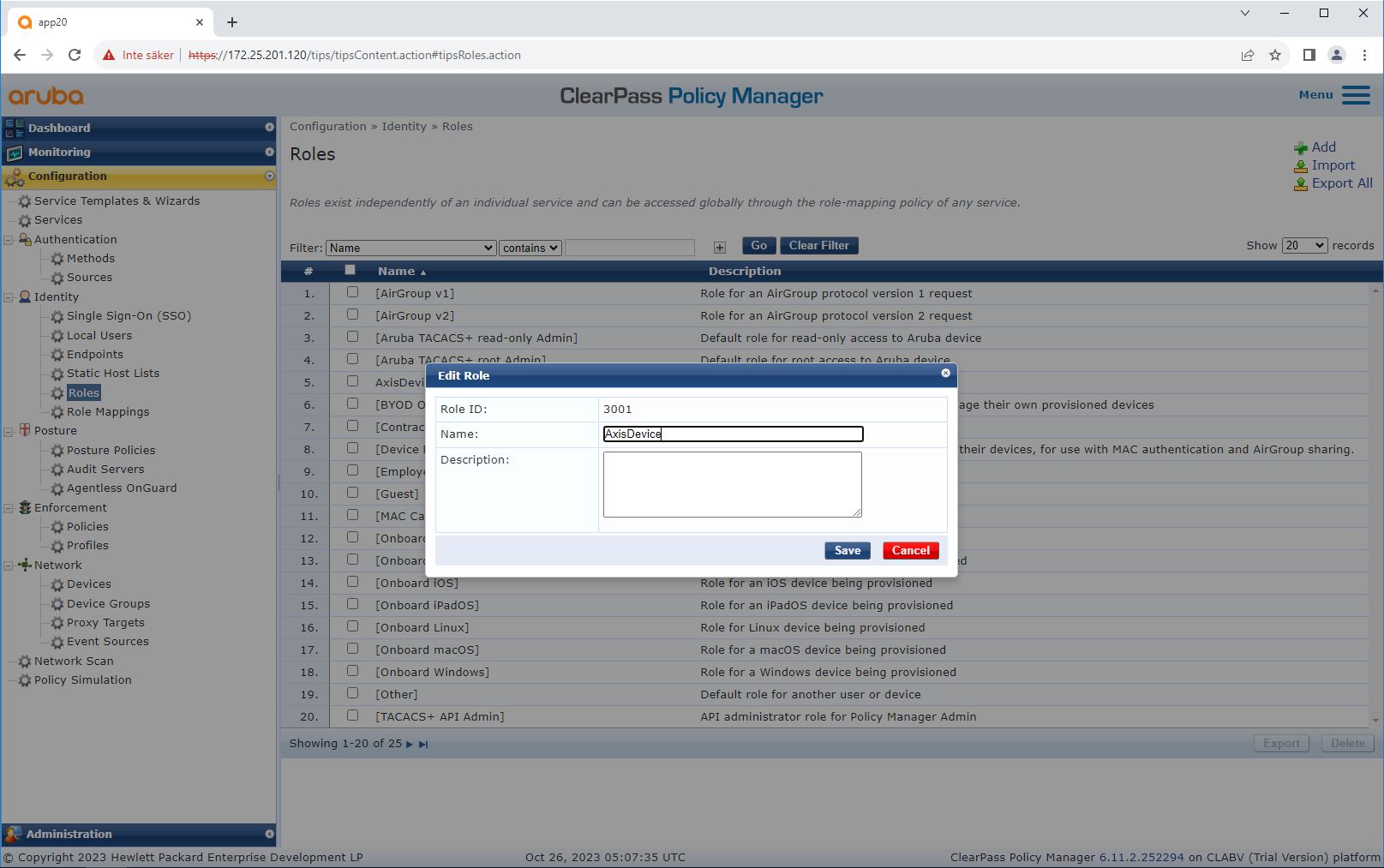
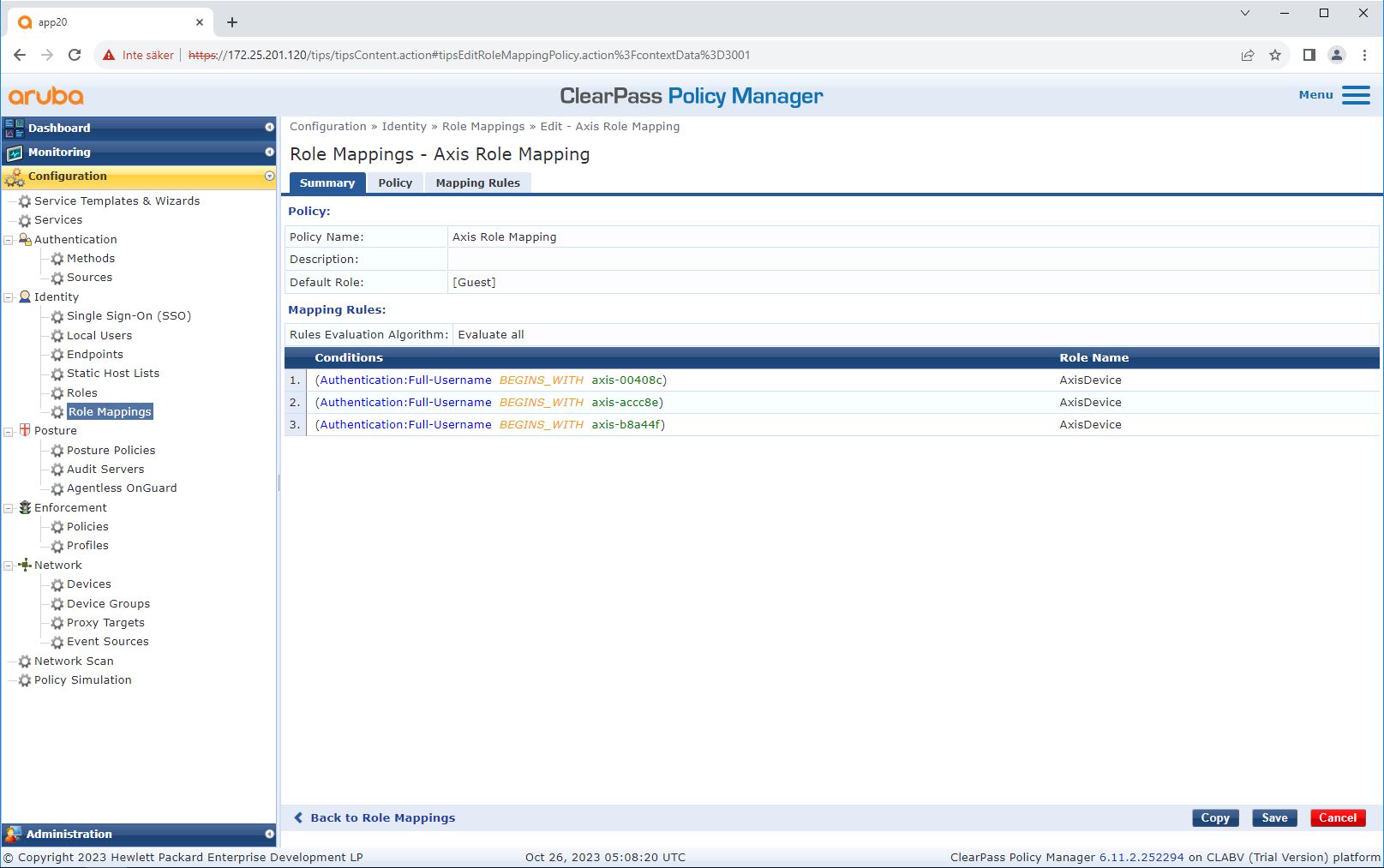
By default, Axis devices use the EAP identity format “axis-serialnumber”. The serial number of an Axis device is its MAC-address. For example “axis-b8a44f45b4e6”.
Service configuration
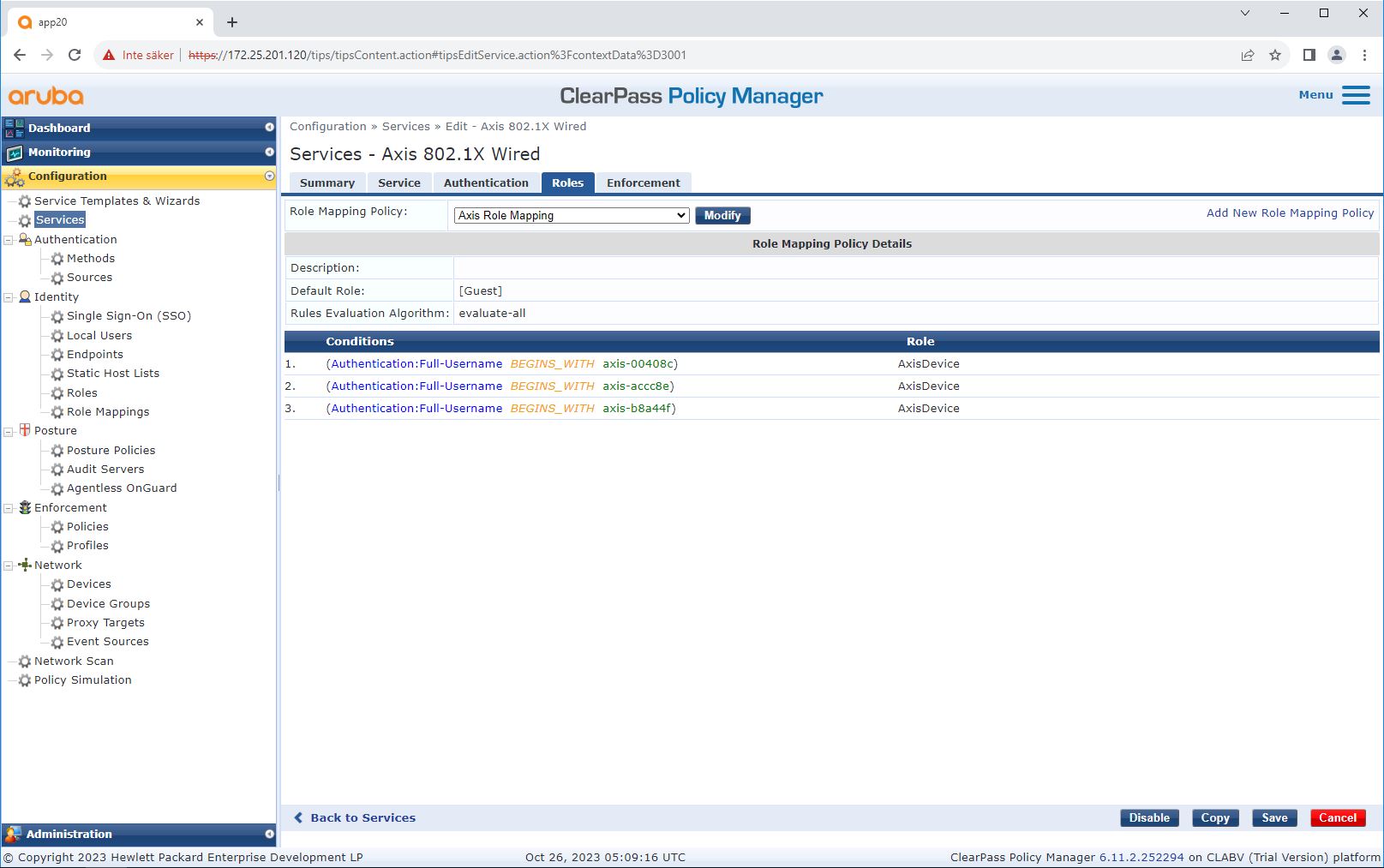
Enforcement profile
HPE Aruba Networking access switch
In addition to the secure onboarding configuration described in HPE Aruba Networking access switch, see below the example port configuration for the HPE Aruba Networking access switch to configure IEEE 802.1AE MACsec.
macsec policy macsec-eap
cipher-suite gcm-aes-128port-access role AxisDevice
associate macsec-policy macsec-eap
auth-mode client-modeaaa authentication port-access dot1x authenticator
macsec
mkacak-length 16
enableCertificate management – Enrollment over Secure Transport (EST)
Digital certificates are critical for securing devices and networks, but managing them can be complex and time-consuming. Certificates expire and must be renewed regularly. Without automation, this process is repetitive and manual, especially in large deployments or environments with mixed device types.
AXIS OS 12.9 introduces support for Enrollment over Secure Transport (EST), which is a protocol for securely provisioning certificates to devices. Defined in RFC 7030, EST is a standard-based solution designed to simplify and automate the full certificate lifecycle, including:
Enrollment – securely issuing new certificates to devices
Renewal – automatically replacing expiring certificates
Re-enrollment – updating certificates based on IT policies
EST supports IT-defined policies for certificate attributes, such as validity period, key type (RSA/ECC) or the key size and it uses HTTPS exclusively.
Key benefits of EST
IT-policy managed automated certificate enrollment, renewal, and re-enrollment removing entirely the need for manual, time-consuming configuration.
State-of-the-art secure communication via HTTPS-only TLS 1.2/1.3.
Centralized visibility/monitoring for IT teams.
Standard-based (RFC 7030) and integrates with IT-infrastructure.
Scalable solution for IoT, enterprise networks, and device management.
Please refer to our AXIS OS Knowledge Base for the general EST documentation.
Configuration HPE Aruba ClearPass Onboard
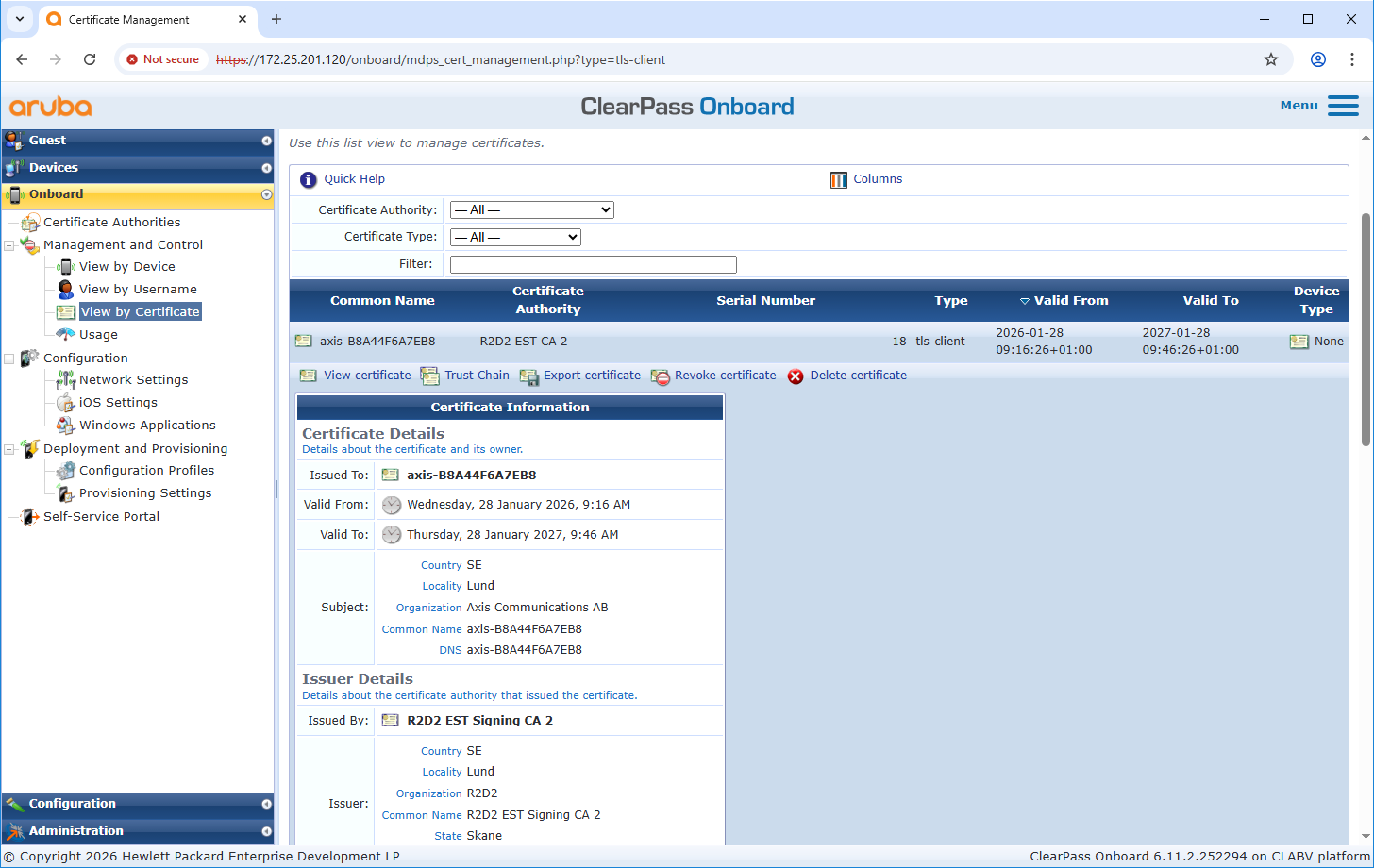
Aruba ClearPass Onboard integrates with EST to securely distribute and manage device certificates for network access. Using EST, endpoints authenticate to ClearPass and enroll for a unique certificate over a secure TLS channel, which is then used for 802.1X certificate-based authentication and other services. This provides a standards-based, automated, and password-less method for enforcing secure access policies based on device identity.
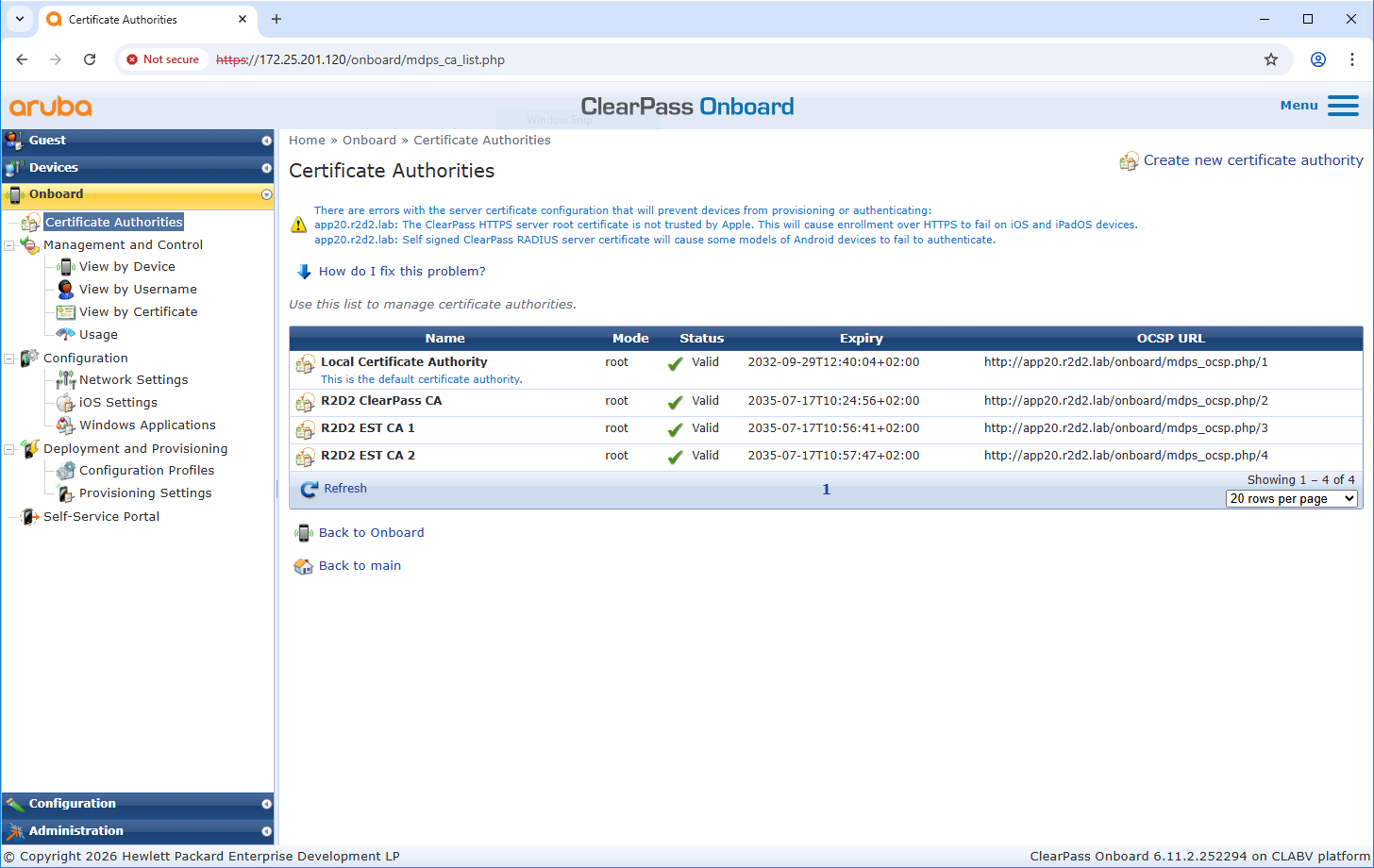
Certificate authority configuration
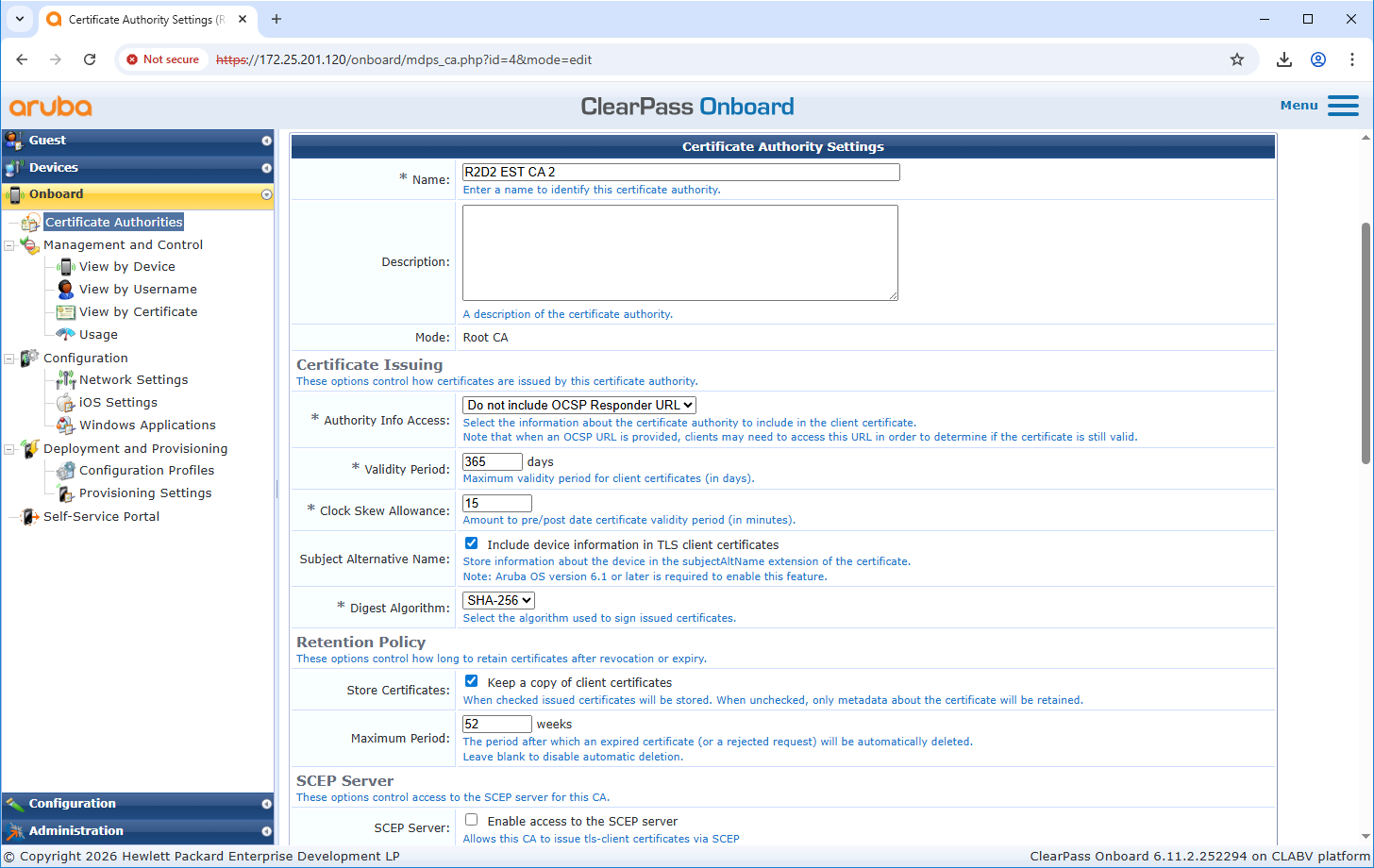
Configuration HPE Aruba ClearPass Policy Manager
Trusted certificate store configuration
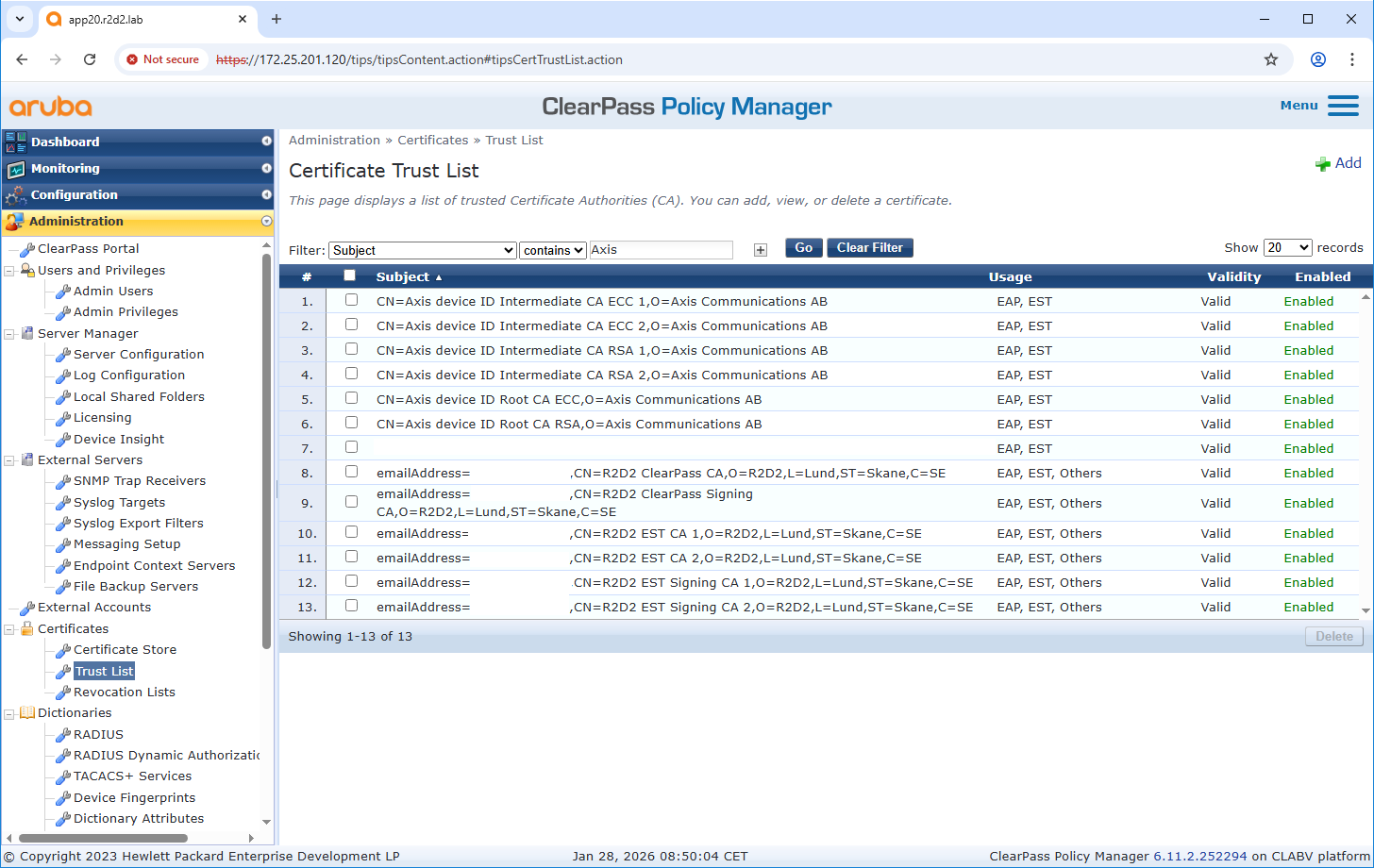
If not already done, upload the Axis-specific IEEE 802.1AR certificates to the trusted certificate store of ClearPass Policy Manager. Ensure that EST usage is added. Verify this also for the previously created certificate authority from ClearPass Onboard.
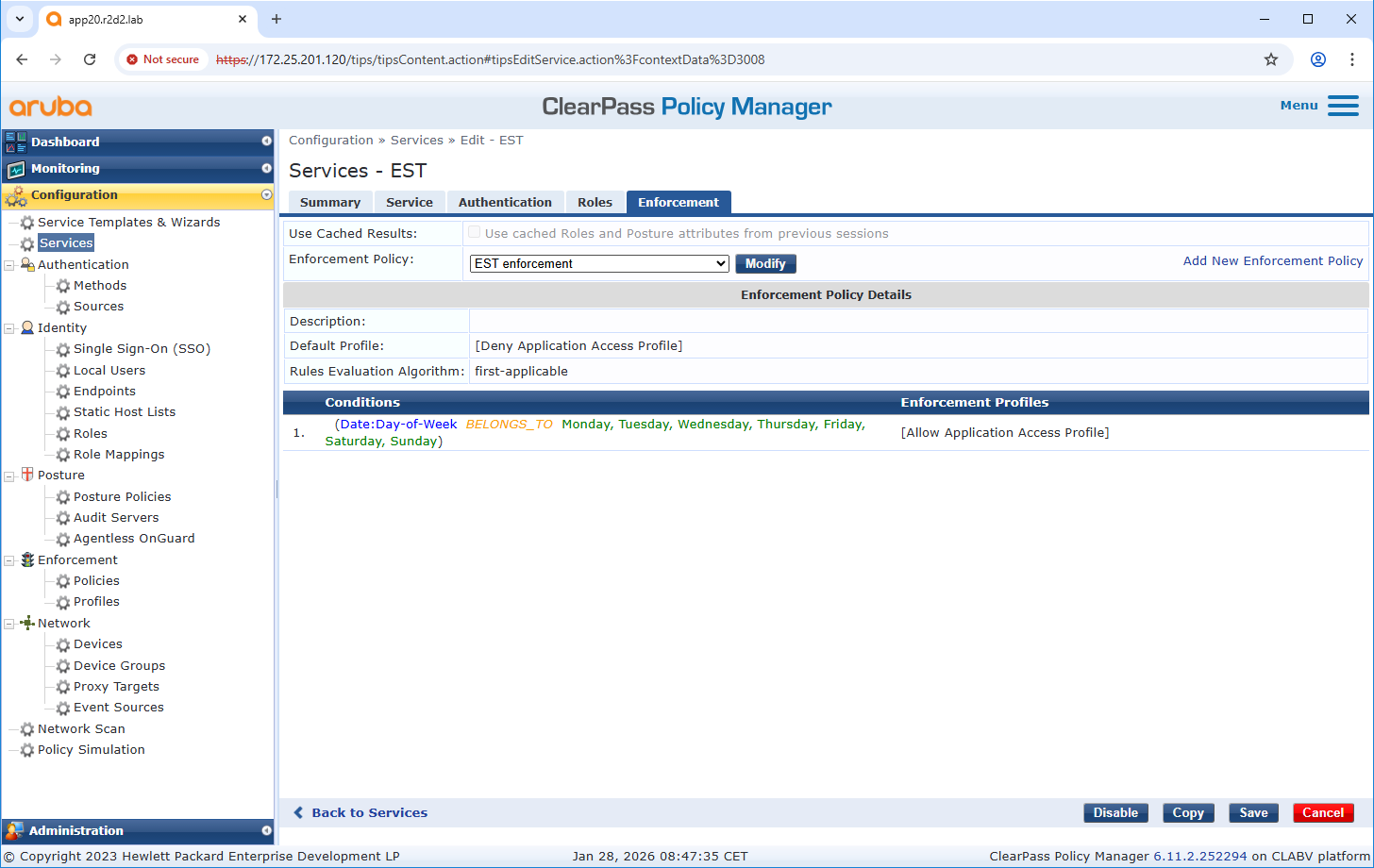
Enforcement policy configuration
Enforcement Profile allows ClearPass Policy Manager to assign specific enforcements to the EST application. For example, new certificates can only be enrolled from specific endpoints or only on specific days of the week.
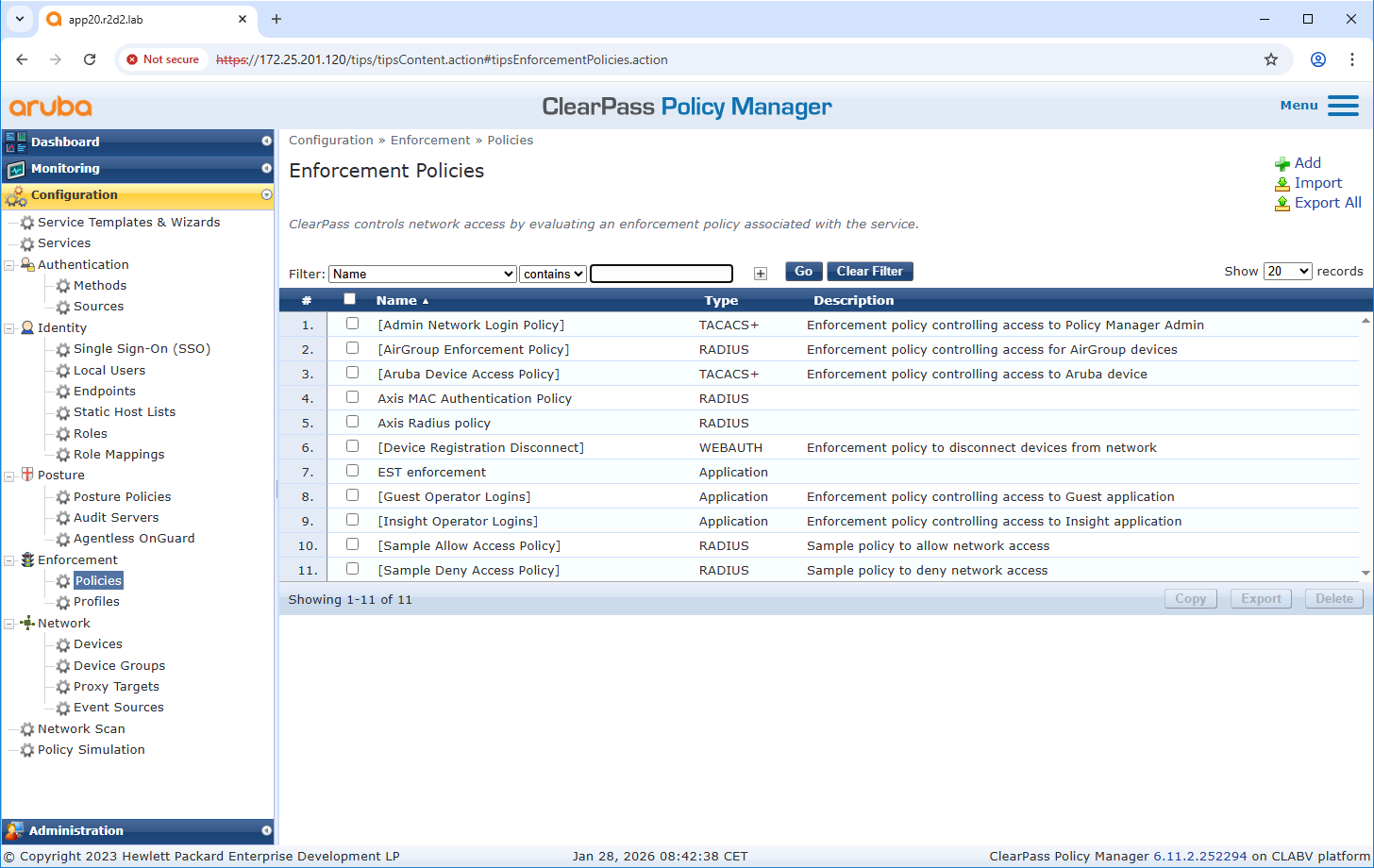
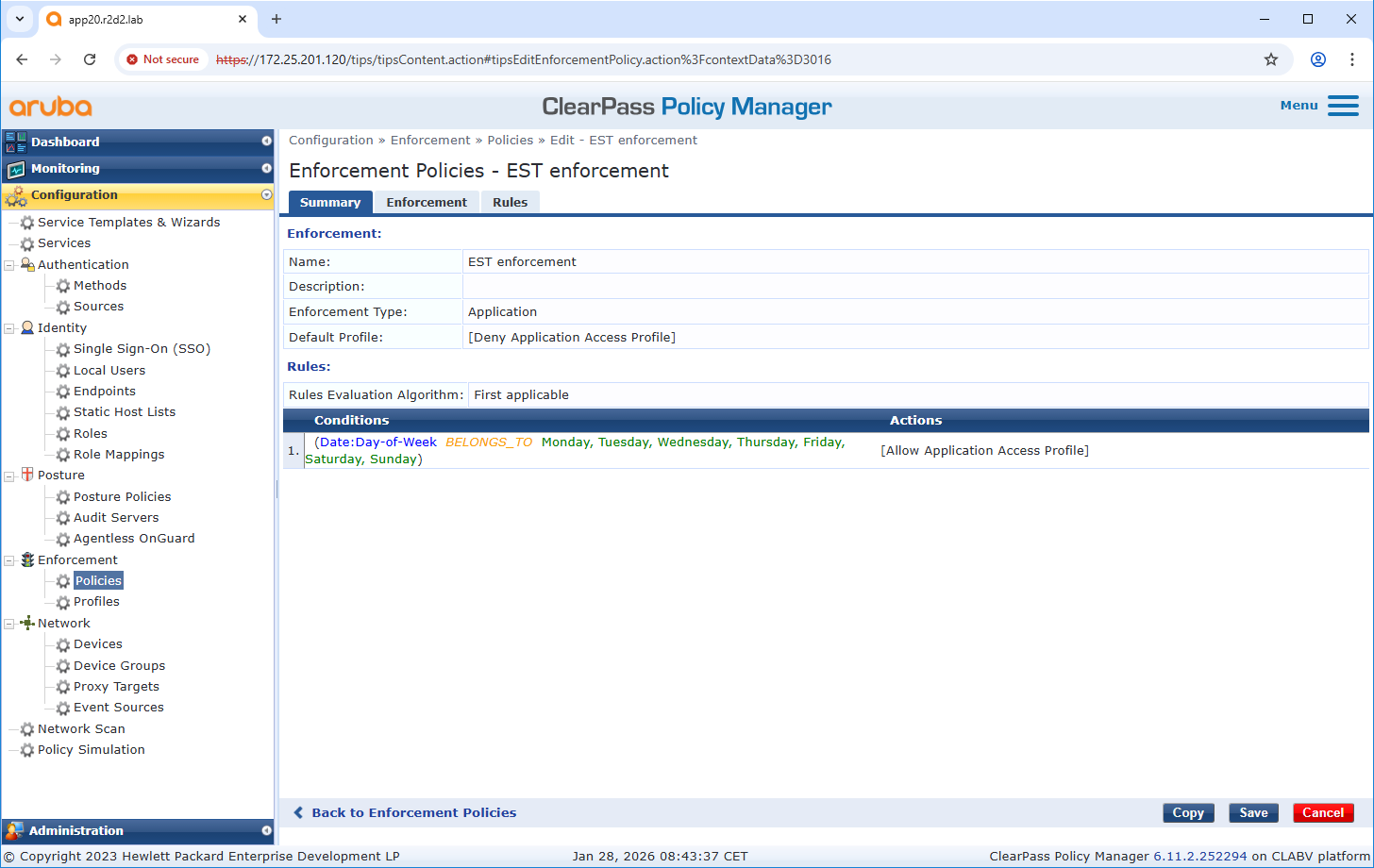
Service configuration
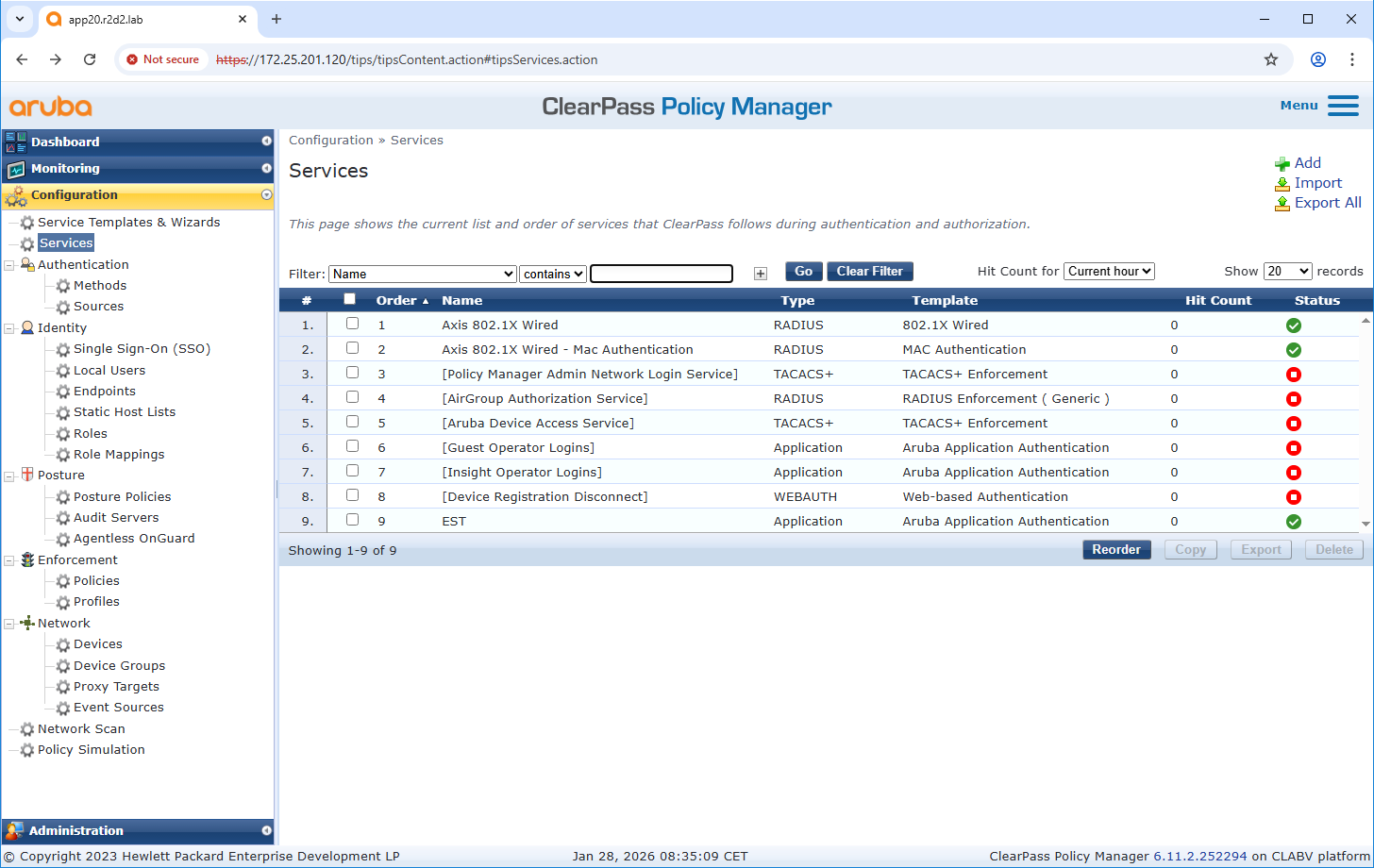
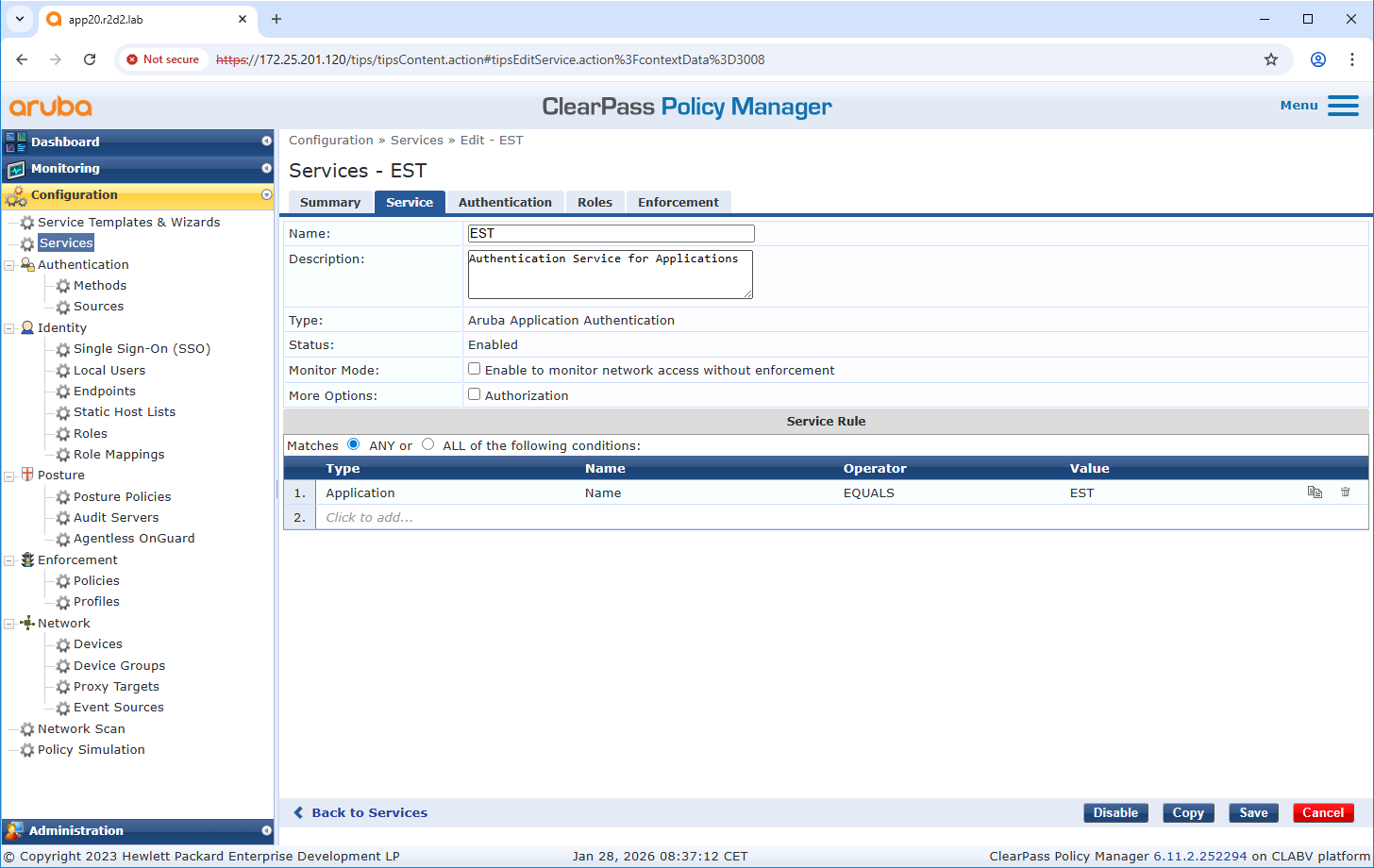
Configuration Axis
The configuration on the Axis device is made in two steps.
Establish trust with the ClearPass Onboard HTTPS endpoint.
Configure the EST client on the Axis device.
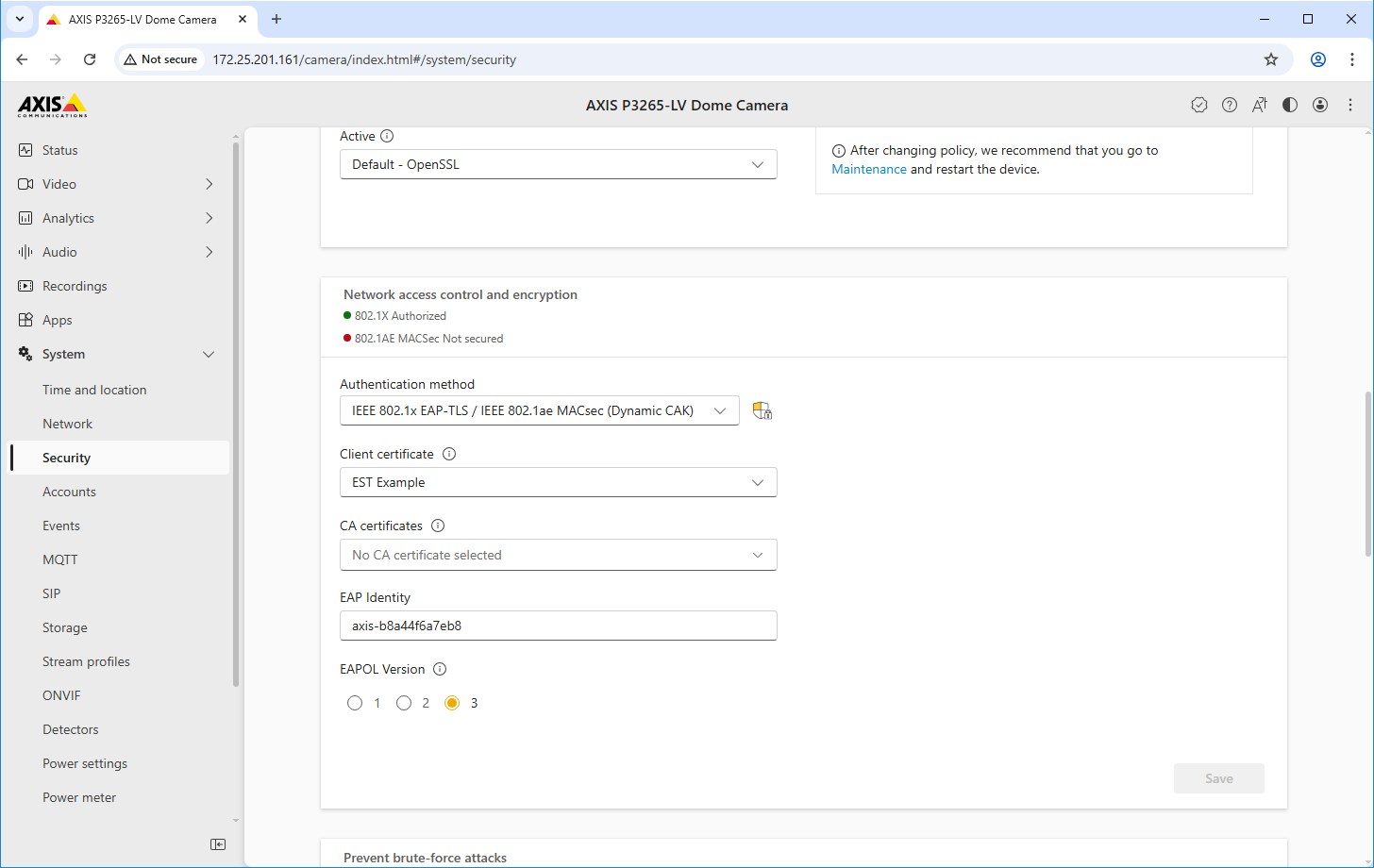
Trusted certificate configuration
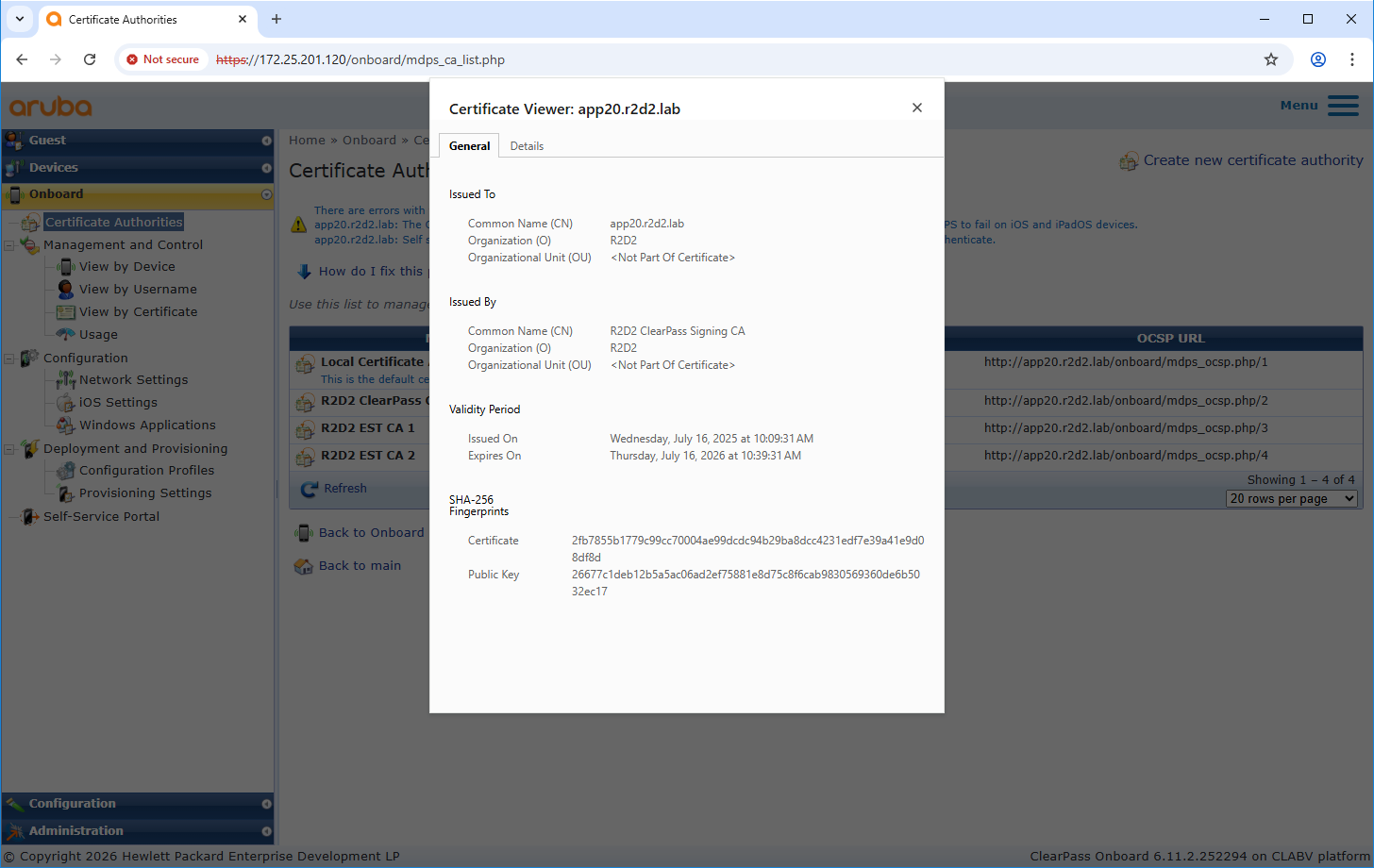
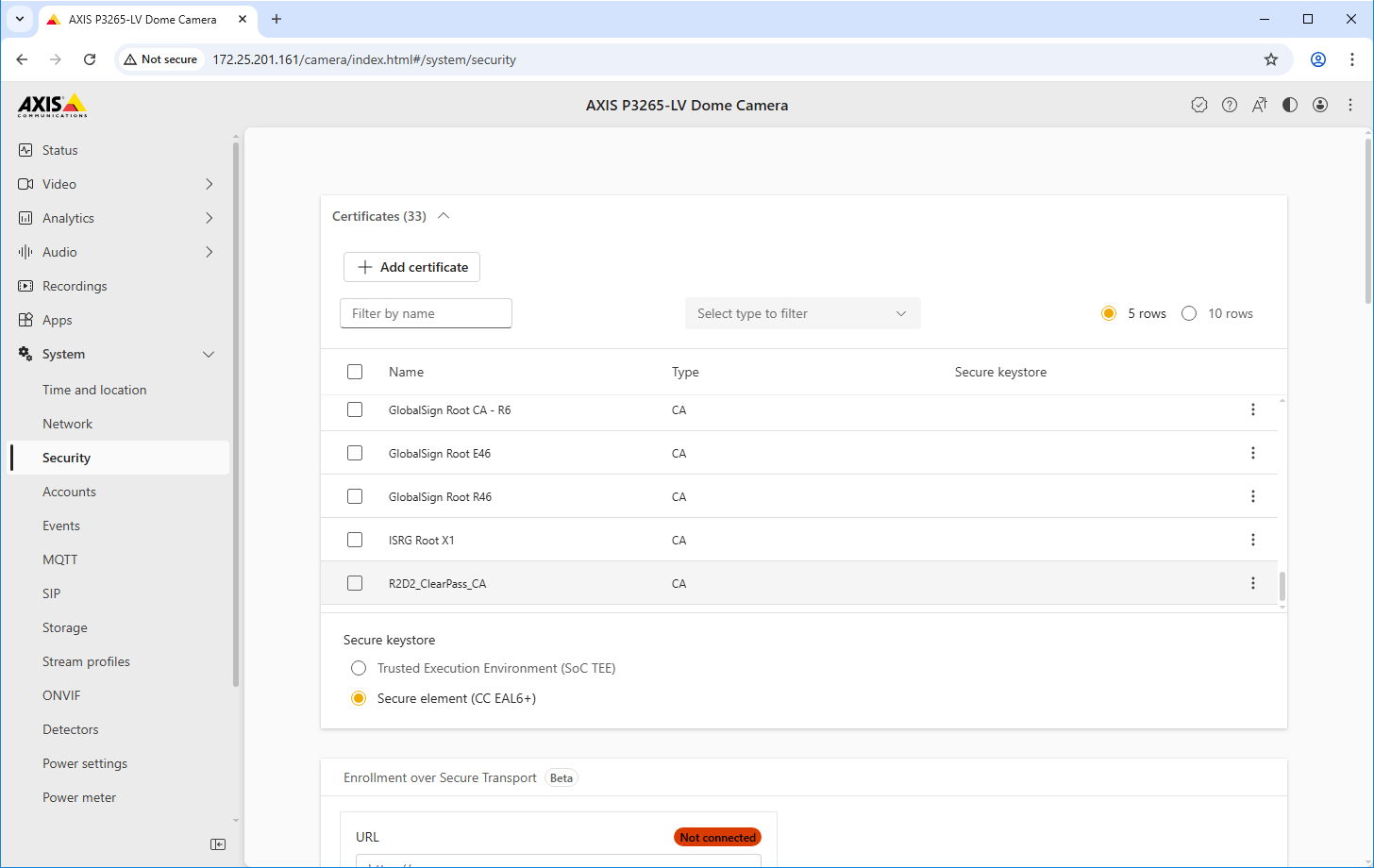
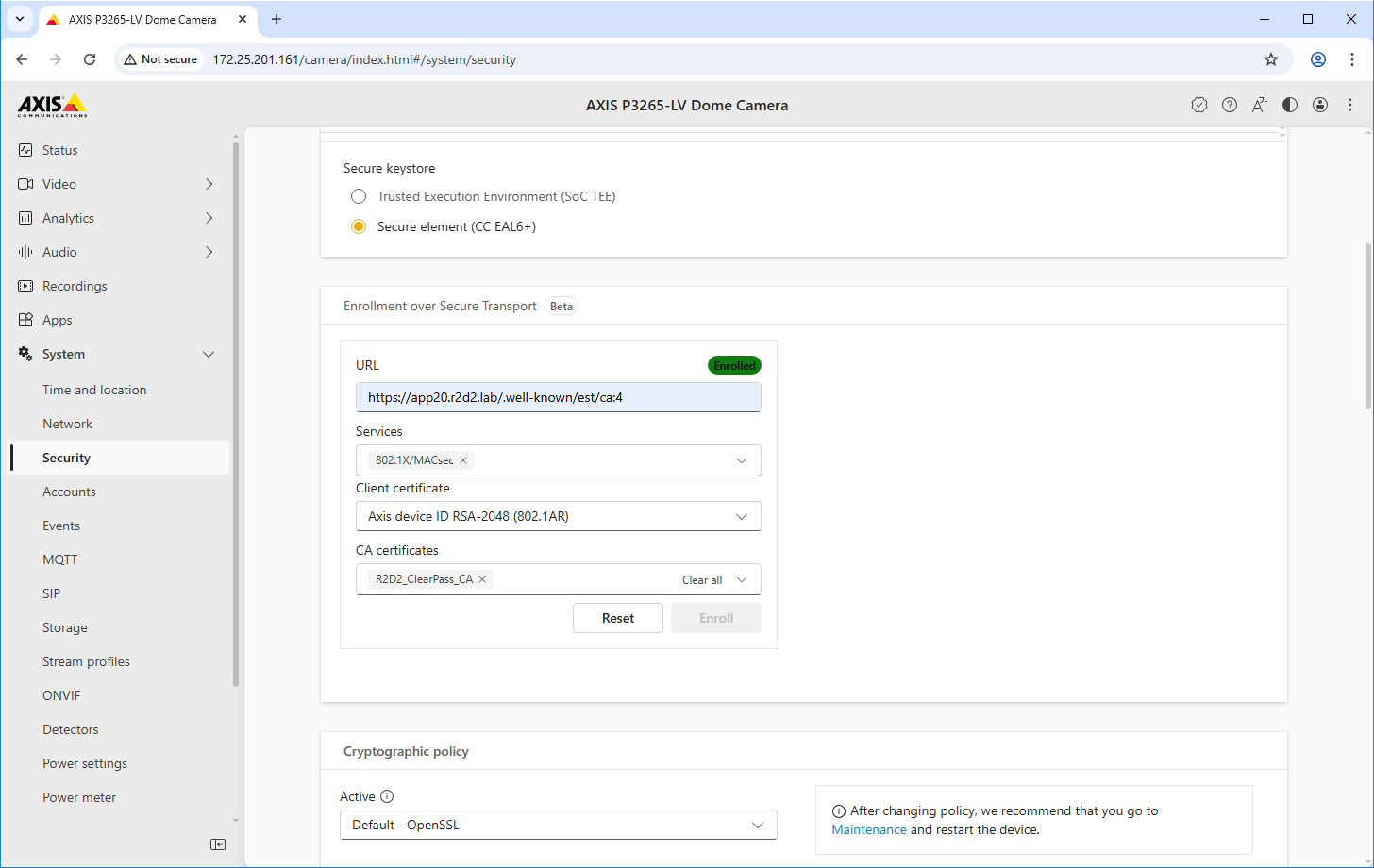
EST client configuration
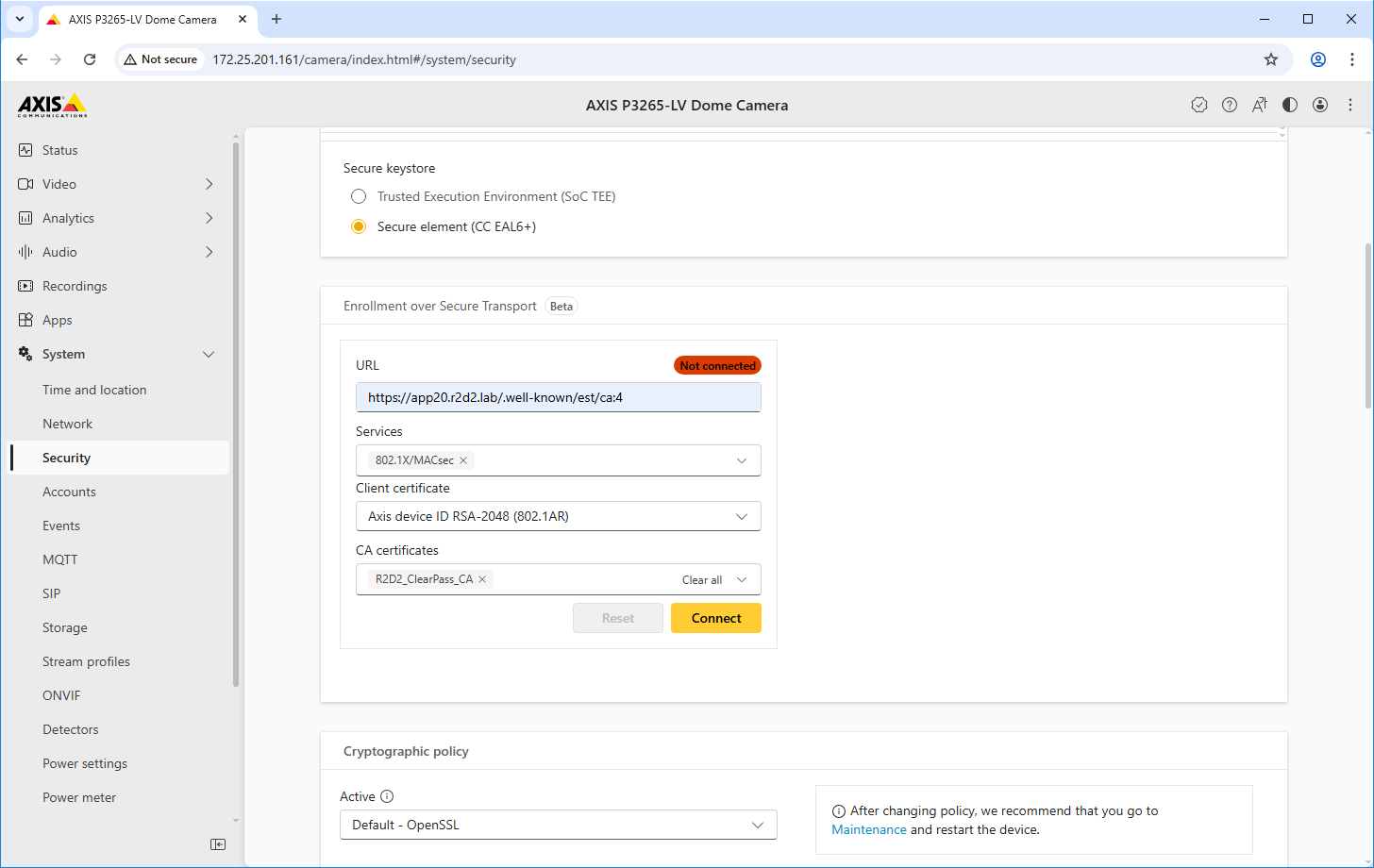
Parameter | Value |
URL | The EST URL can be found in the created certificate authority for EST in ClearPass Onboard. |
Services | Select the services that should automatically be configured with the enrolled certificate. |
Client certificate | Select a client certificate for the authentication against the ClearPass Onboard EST server. Devices with the Axis Device ID are automatically trusted for enrollment, as the Axis-specific IEEE 802.1AR certificate chain was added to the trusted certificate store in ClearPass Policy Manager. |
CA certificates | Select the CA certificate from the ClearPass Onboard HTTPS endpoint so that the Axis device trusts that endpoint. |
Legacy onboarding - MAC authentication
You can use MAC Authentication Bypass (MAB) to onboard Axis devices that don’t support IEEE 802.1AR onboarding with the Axis device ID certificate and IEEE 802.1X enabled in the factory default state. If 802.1X onboarding fails, ClearPass Policy Manager validates the Axis device’s MAC address and grants access to the network.
MAB requires both access switch and ClearPass Policy Manager configuration preparations. No configuration is required on the Axis device to allow MAB for onboarding.
HPE Aruba Networking ClearPass Policy Manager
Enforcement policy
The enforcement policy configuration in ClearPass Policy Manager defines if Axis devices are granted access to HPE Aruba Networking powered networks based on the following two example policy conditions.
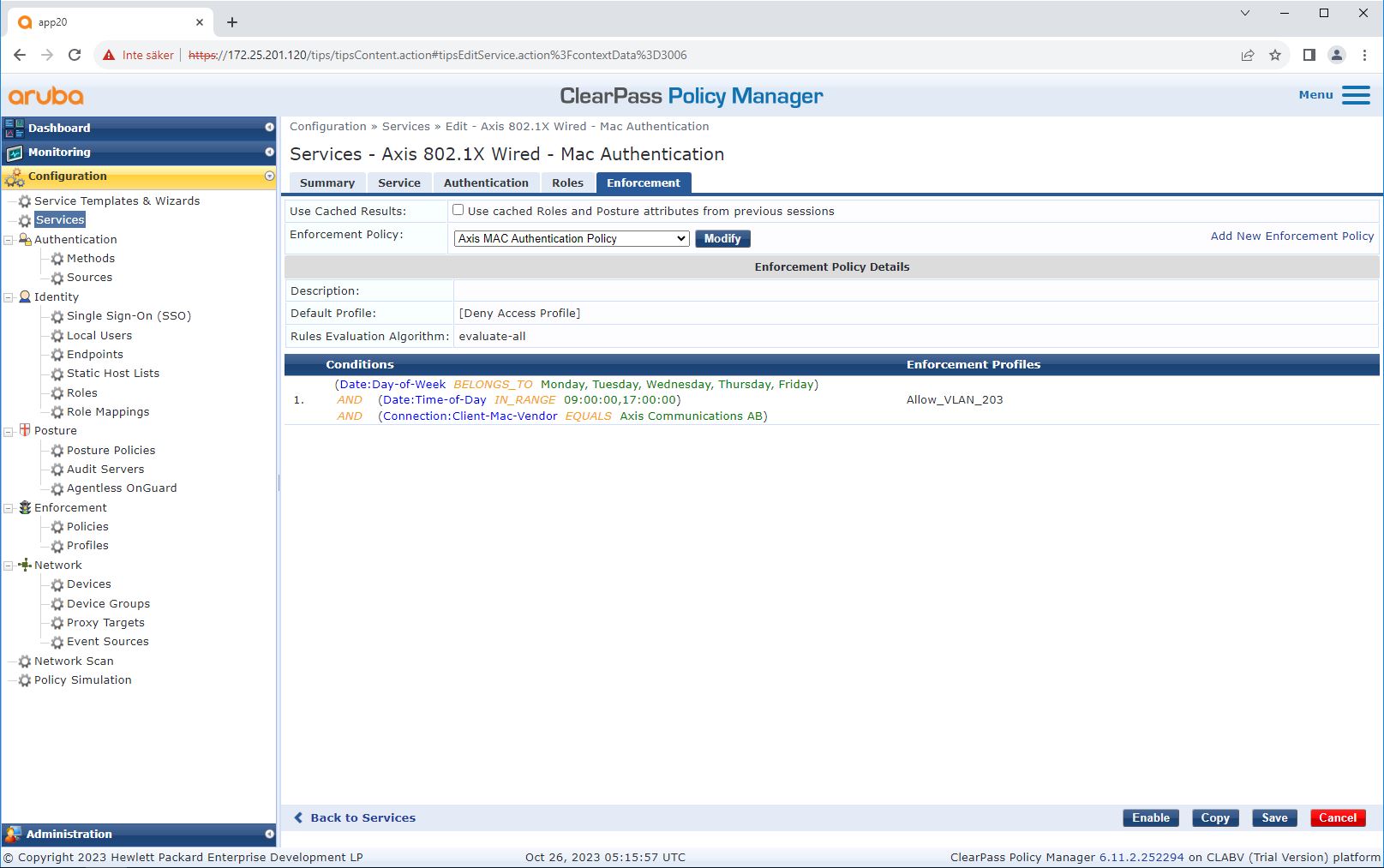
Denied network access
If the Axis device does not meet the configured enforcement policy, it is denied access to the network.
Guest-network (VLAN 203)
The Axis device is granted access to a limited, isolated network if the following conditions are met:
The day is a weekday, Monday to Friday
The time is between 09:00 and 17:00
The MAC address vendor matches Axis Communications.
As it’s possible to spoof a MAC addresses, access to the regular provisioning network is not granted. We recommend that you only use MAB for initial onboarding, and then manually inspect the device further.
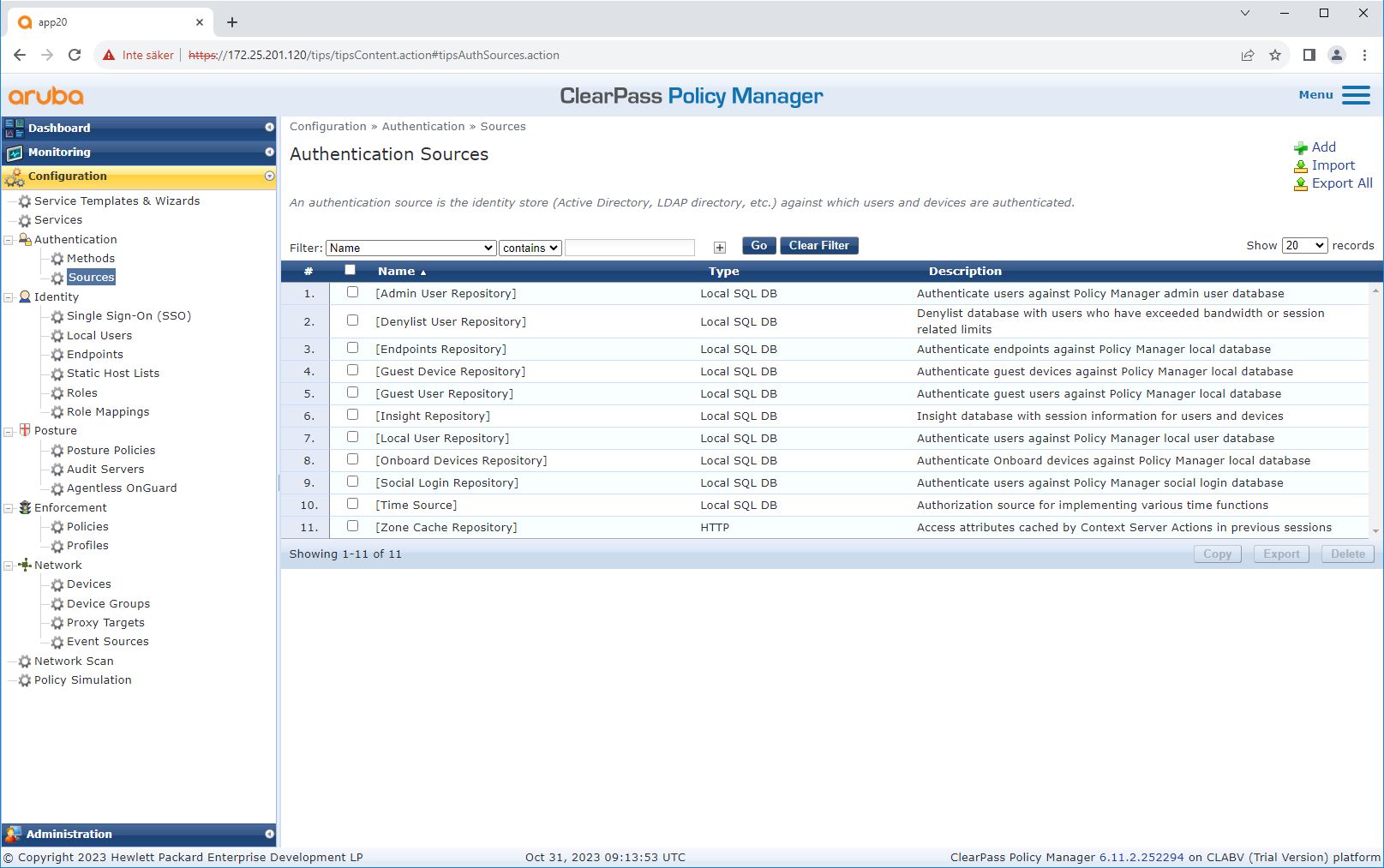
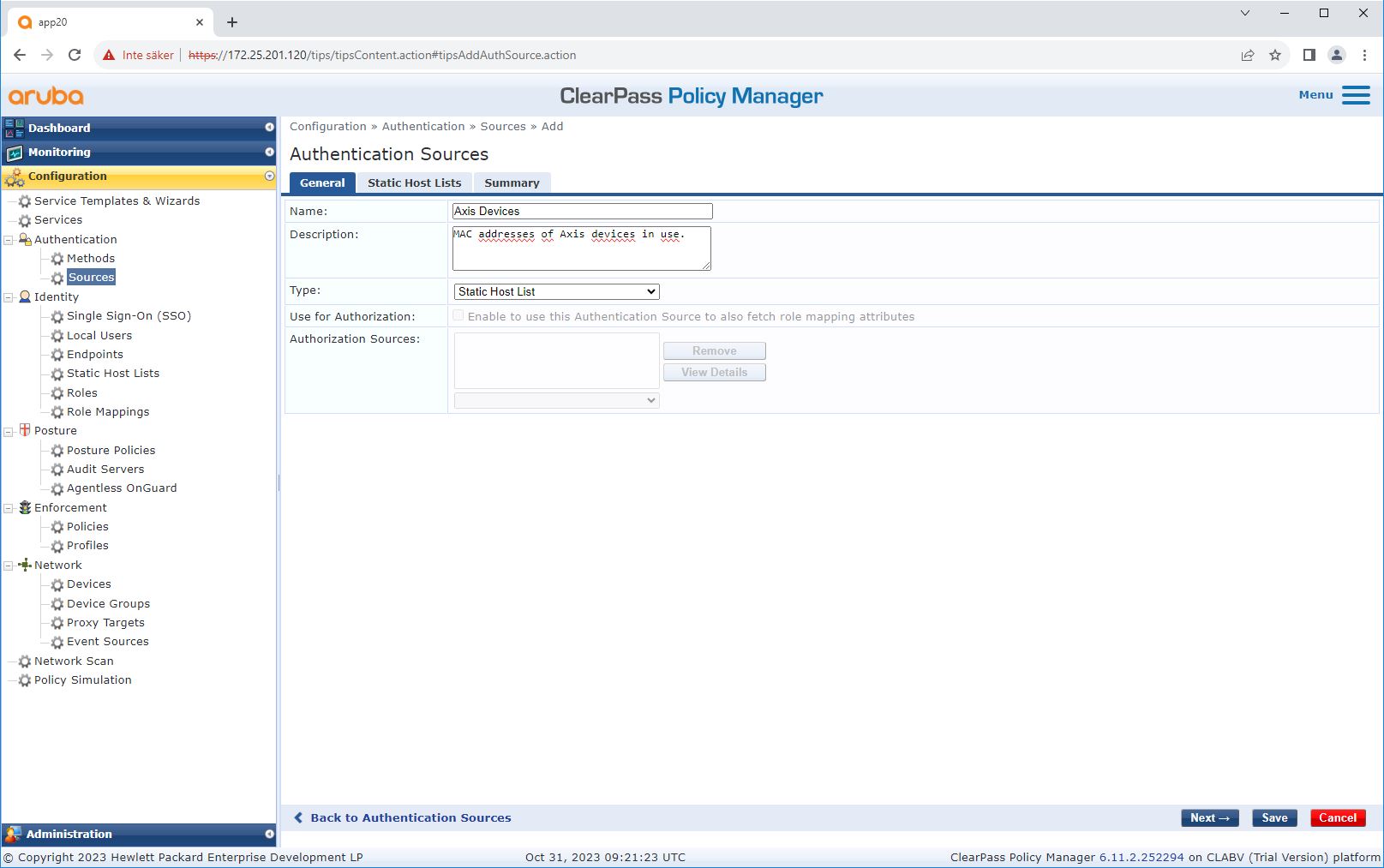
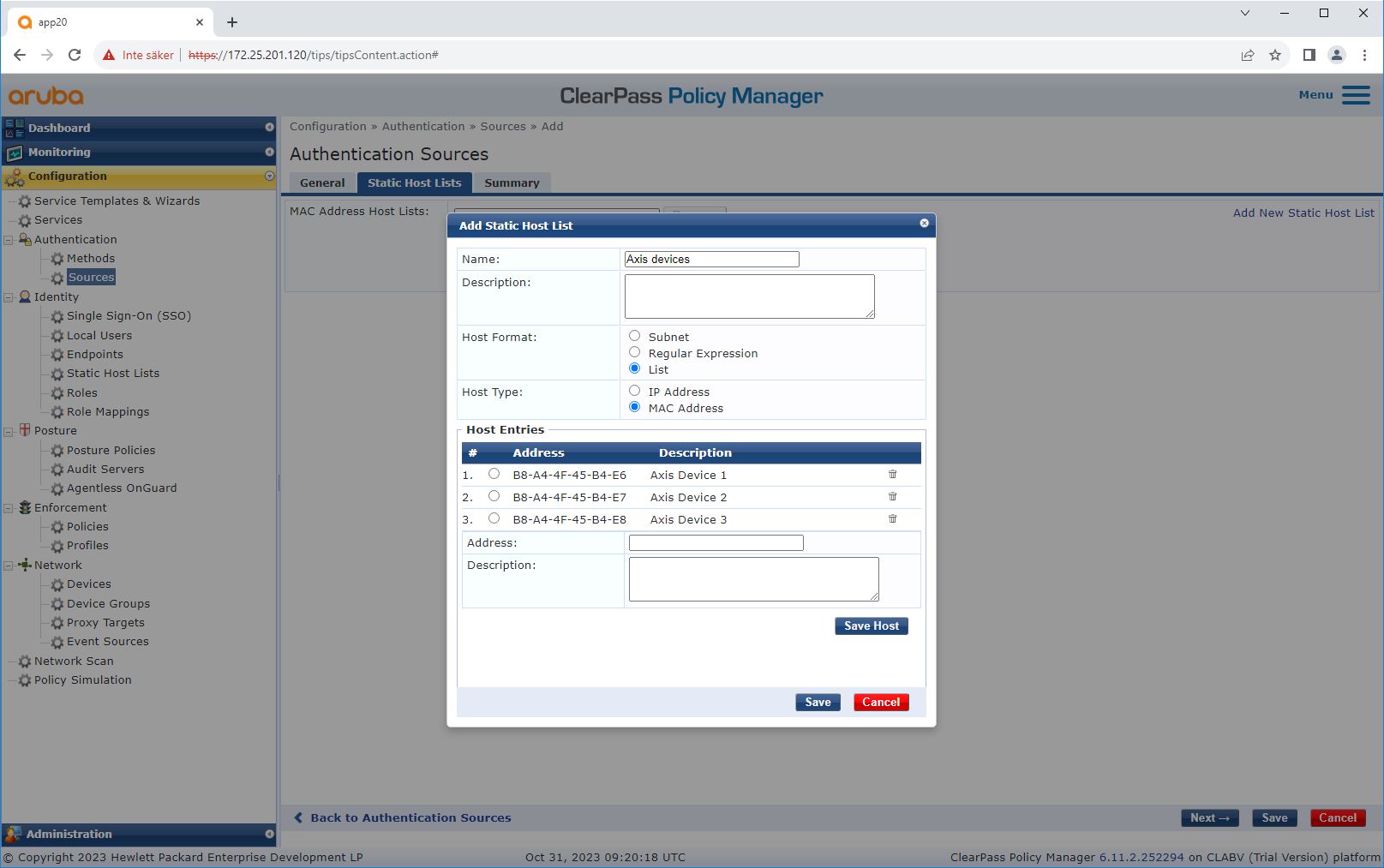
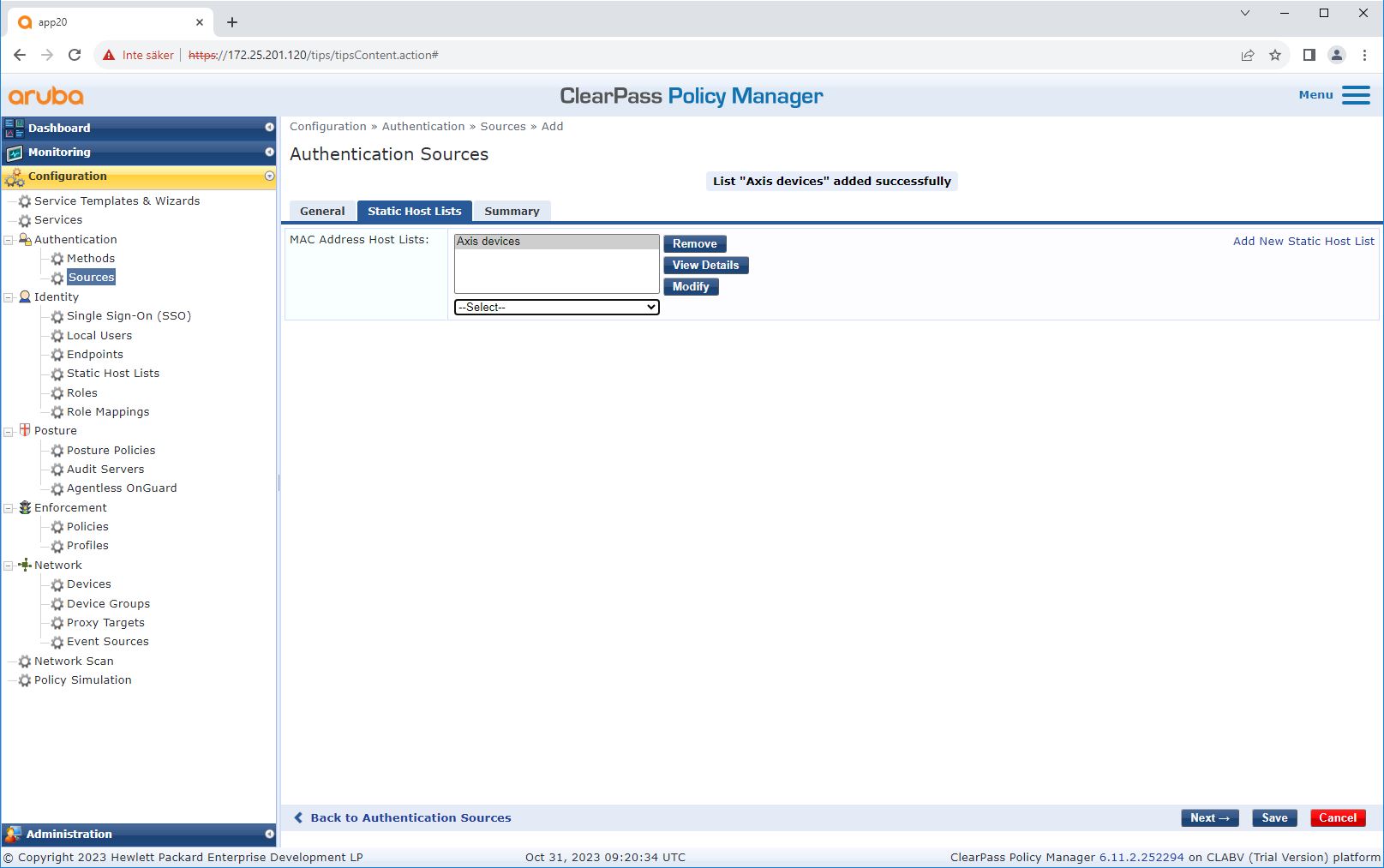
Source configuration
On the Sources page, a new authentication source is created to allow only manually imported MAC addresses.
Service configuration
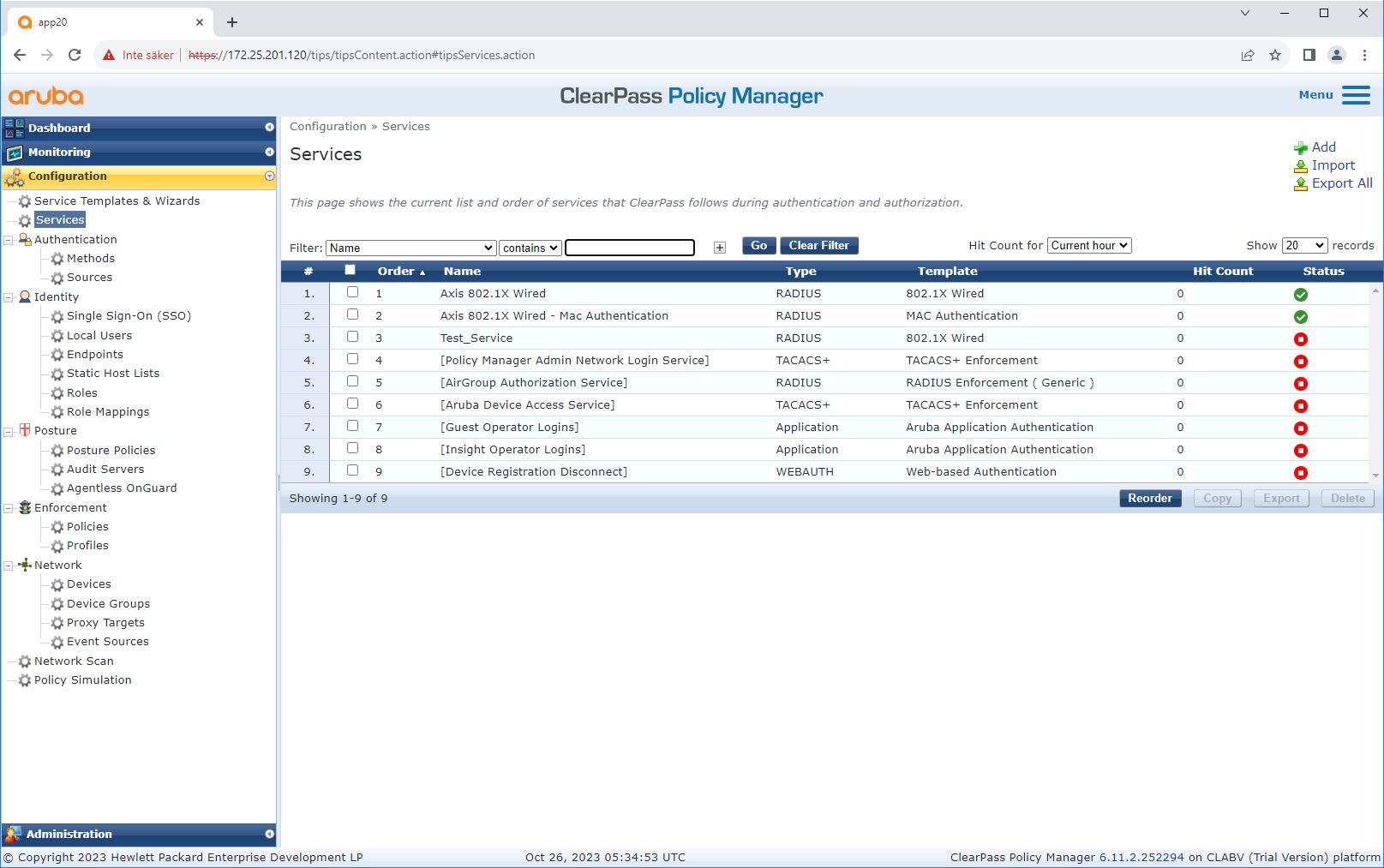
On the Services page, the configuration steps are combined into a single service that handles the authentication and authorization of Axis devices in HPE Aruba Networking networks.
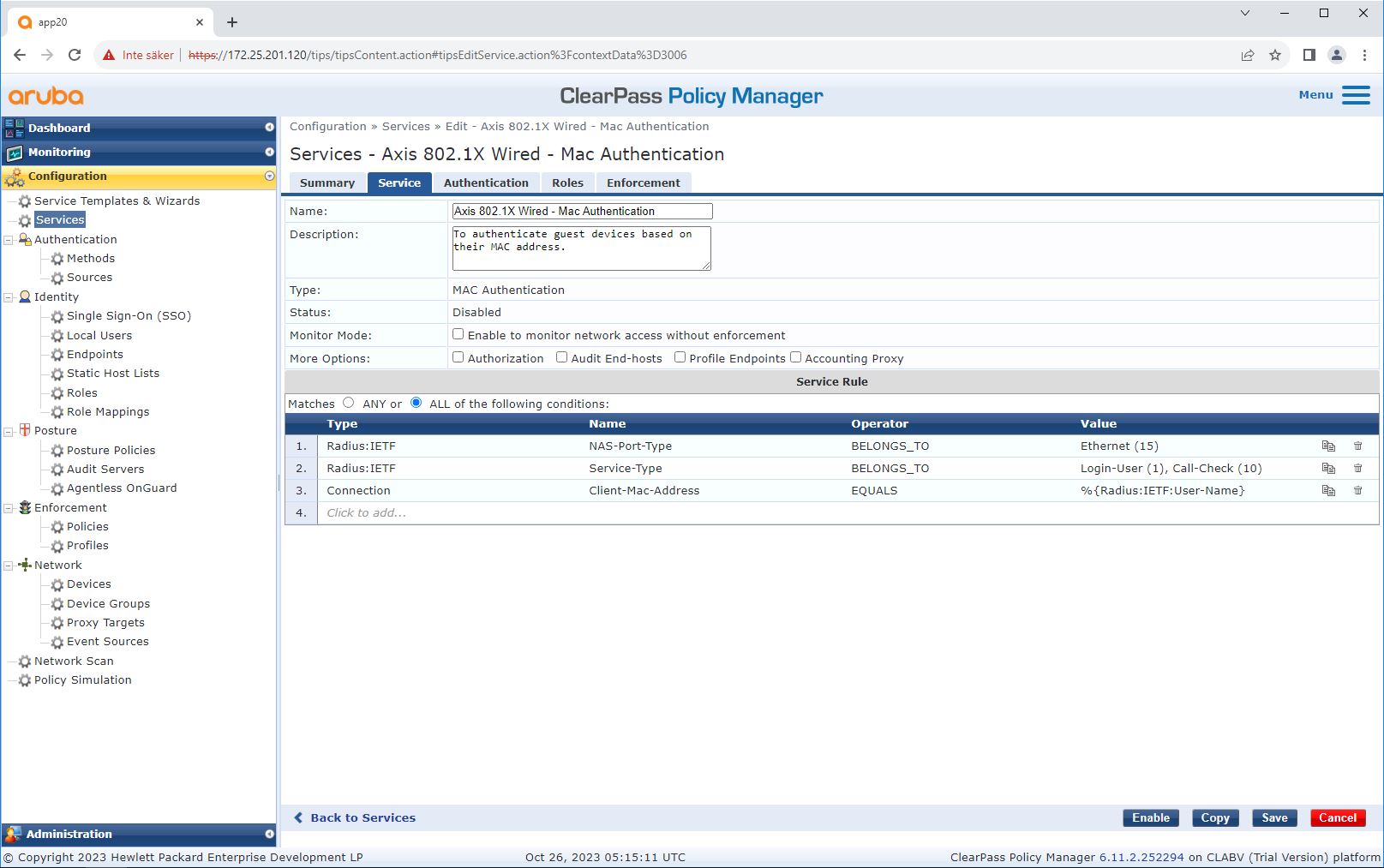
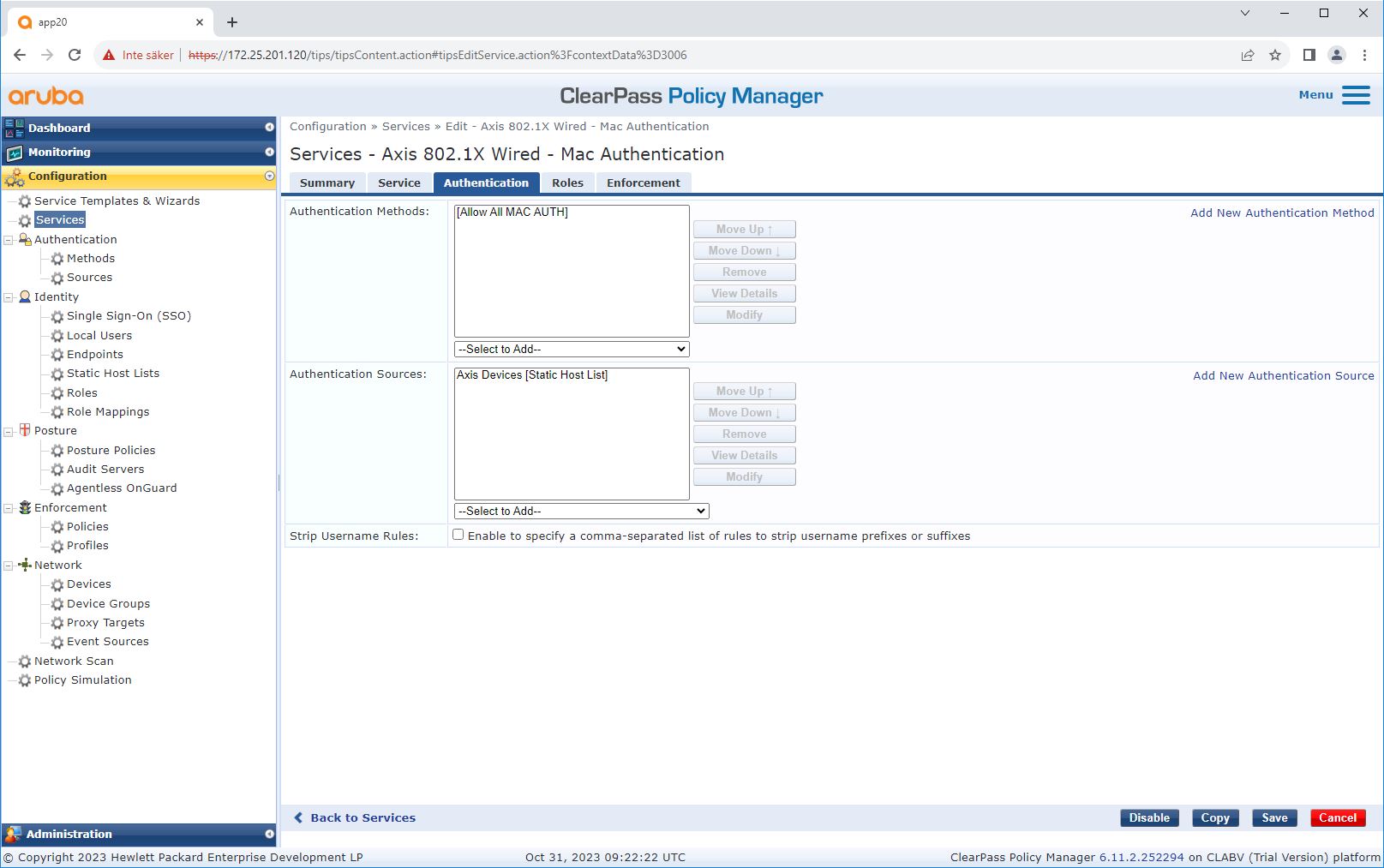
Axis Communications uses the following MAC address OUIs:
B8:A4:4F:XX:XX:XX
AA:C8:3E:XX:XX:XX
00:40:8C:XX:XX:XX

HPE Aruba Networking access switch
In addition to the secure onboarding configuration described in HPE Aruba Networking access switch, see the below example port configuration for the HPE Aruba Networking access switch to allow for MAB.
aaa port-access authenticator 18 tx-period 5
aaa port-access authenticator 19 tx-period 5
aaa port-access authenticator 18 max-requests 3
aaa port-access authenticator 19 max-requests 3
aaa port-access authenticator 18 client-limit 1
aaa port-access authenticator 19 client-limit 1
aaa port-access mac-based 18-19
aaa port-access 18 auth-order authenticator mac-based
aaa port-access 19 auth-order authenticator mac-based
aaa port-access 18 auth-priority authenticator mac-based
aaa port-access 19 auth-priority authenticator mac-based