Introduzione
La sicurezza informatica diventa sempre più importante nei settori della sicurezza e della sorveglianza. Per una sicurezza informatica efficace è necessario garantire una profondità di difesa sufficiente a proteggere adeguatamente la rete IP a ogni livello, dai prodotti e dai partner scelti, ai requisiti stabiliti dal cliente e dai suoi partner.
Questa guida descrive come utilizzare AXIS Device Manager per rendere più sicuro il sistema e aumentare la sicurezza. Si concentra sugli aspetti chiave e descrive le raccomandazioni.
Gestione del ciclo di vita del dispositivo
Noi di Axis siamo consapevoli dell'importanza di una solida base di sicurezza per l'intero ciclo di vita del dispositivo. Il nostro impegno per la sicurezza informatica garantisce che i nostri prodotti e le nostre soluzioni forniscano una solida protezione contro le potenziali minacce.
Implementazione
Axis offre dispositivi sicuri per progettazione con funzioni di sicurezza integrate, come meccanismi di avvio sicuri, sistema operativo firmato e archiviazione crittografata. Inoltre, AXIS Device Manager aiuta gli installatori e gli amministratori di sistema a configurare e distribuire in modo sicuro i dispositivi, garantendo una configurazione sicura fin dall'inizio.
Servizio attivo
Durante la fase operativa, Axis offre aggiornamenti regolari del software del dispositivo e patch di sicurezza per proteggere dalle vulnerabilità. AXIS Device Manager consente inoltre il monitoraggio e la manutenzione da remoto, permettendo una rapida risoluzione dei problemi e tempi di inattività minimi. Inoltre, le nostre guide all'hardening forniscono consigli per configurare i dispositivi in modo da soddisfare specifici requisiti di sicurezza.
Smaltimento
Quando è il momento di dismettere o sostituire i dispositivi, AXIS Device Manager facilita la dismissione sicura cancellando i dati sensibili e ripristinando i dispositivi alle impostazioni di fabbrica. Ciò garantisce che nessuna informazione riservata rimanga sul dispositivo, proteggendo i dati dell'utente e impedendo l'accesso non autorizzato.
AXIS Device Manager
AXIS Device Manager è uno strumento locale che fornisce un modo semplice, economico e sicuro dal punto di vista informatico per gestire tutte le principali attività di installazione, di sicurezza e manutenzione (vedere la tabella seguente). Lo strumento è adatto per gestire fino a un paio di migliaia di dispositivi Axis in un singolo sito o per diverse migliaia di dispositivi distribuiti in più siti. AXIS Device Manager consente di implementare in modo efficiente i controlli di sicurezza informatica per proteggere i dispositivi di rete e allinearli a un'infrastruttura di sicurezza.
Funzioni di gestione dei dispositivi, AXIS Device Manager
| Installazione | Manutenzione |
| Assegnazione di un indirizzo IP | Stato dispositivi |
| Esportazione dell'elenco dei dispositivi e traccia delle risorse* | Raccolta dei dati dei dispositivi |
| Gestione degli utenti e delle password* | Configurazione e copia delle configurazioni su più dispositivi |
| Gestione ACAP | Connessione a più server/sistemi |
| Aggiornamento del sistema operativo AXIS, basato su LTS o Active*. | Punti di ripristino |
| Gestione dei certificati HTTPS* | Ripristino dei valori predefiniti di fabbrica |
| Gestire i certificati IEEE 802.1*/** | Sostituire il(i) dispositivo(i) |
| Tagging dispositivi | Rinnovo e gestione dei certificati* |
| Protezione avanzata della sicurezza informatica* |
* Indica la funzione di controllo della sicurezza informatica.
** I servizi di certificazione di Active Directory non sono attualmente supportati. Convalidato per FreeRADIUS in esecuzione su Linux.
Inventario del dispositivo
Un aspetto fondamentale per garantire la sicurezza di una rete aziendale è mantenere un inventario completo dei dispositivi che risiedono nella rete. Quando si crea o si rivede un criterio di sicurezza generale, è importante disporre chiaramente delle conoscenze e della documentazione per ciascun dispositivo e non solo sulle risorse critiche. Questo perché ogni dispositivo sottovalutato può essere un varco per i malintenzionati. Non è possibile proteggere i dispositivi che si ignorano o di cui non si è pienamente a conoscenza.
L'inventario dei dispositivi rappresenta un passaggio fondamentale per la protezione della rete aziendale. AXIS Device Manager può essere d'aiuto in questo senso:
Consente di accedere facilmente a un inventario corrente e completo dei dispositivi di rete quando si lavora con controlli e operatori di incidenti.
Fornisce un elenco completo dei dispositivi, che possono essere ordinati per numero totale, tipo, numeri di modello, ecc.
Fornisce lo stato di ogni dispositivo nella rete.
Aiuta a pianificare il futuro, mostrando la data prevista per la fine del supporto software del dispositivo e indicando quali prodotti più recenti possono essere utilizzati in sostituzione.
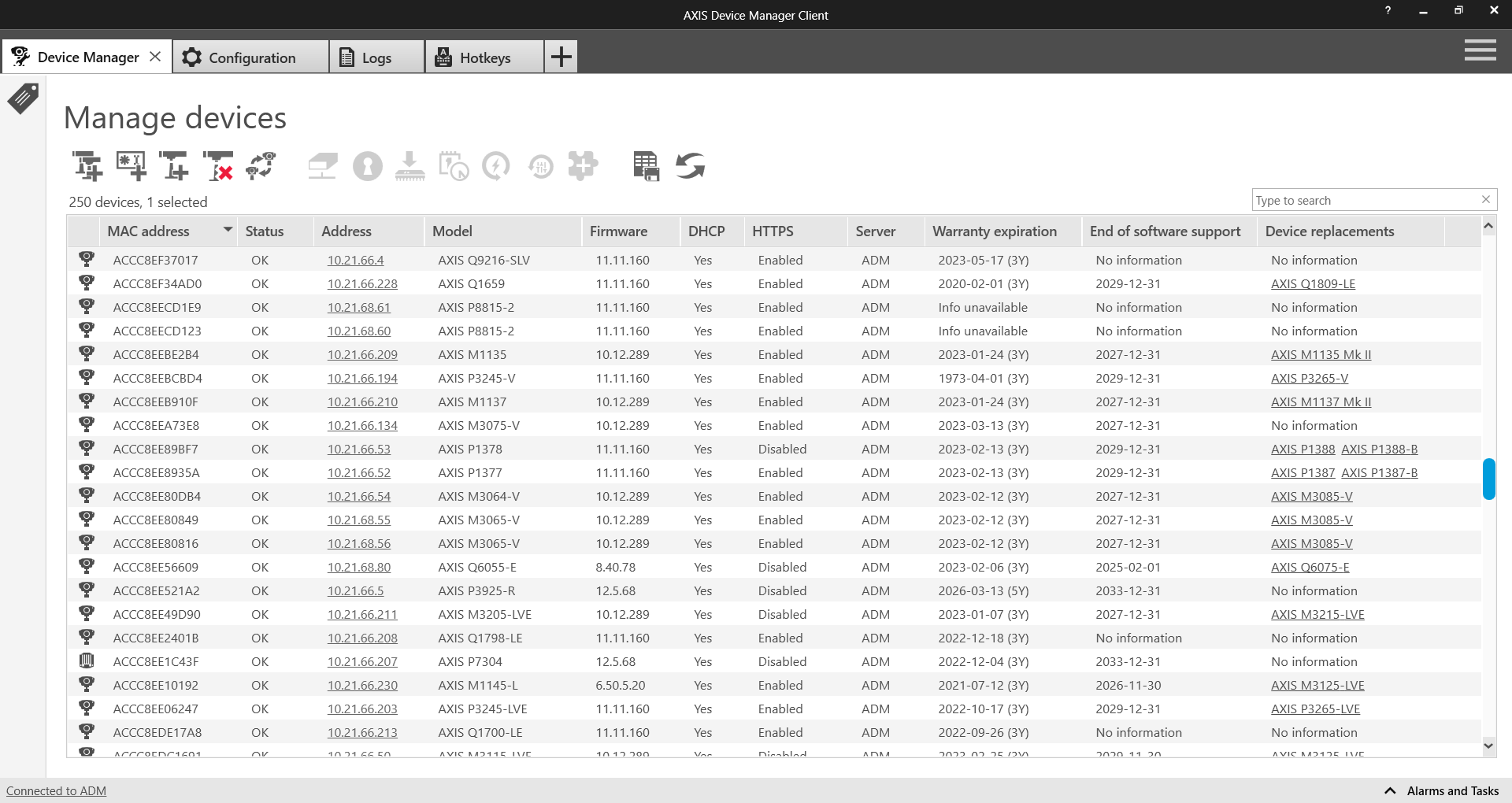
AXIS Device Manager fornisce i mezzi automatizzati per accedere all'inventario dei dispositivi di rete Axis in tempo reale. Consente di identificare, elencare e ordinare automaticamente i dispositivi. Altrettanto importante è la possibilità di utilizzare i tag per raggruppare e ordinare i dispositivi in base ai propri criteri, semplificando la visione d'insieme e la documentazione di tutti i dispositivi Axis presenti sulla rete.
Criteri di account e password
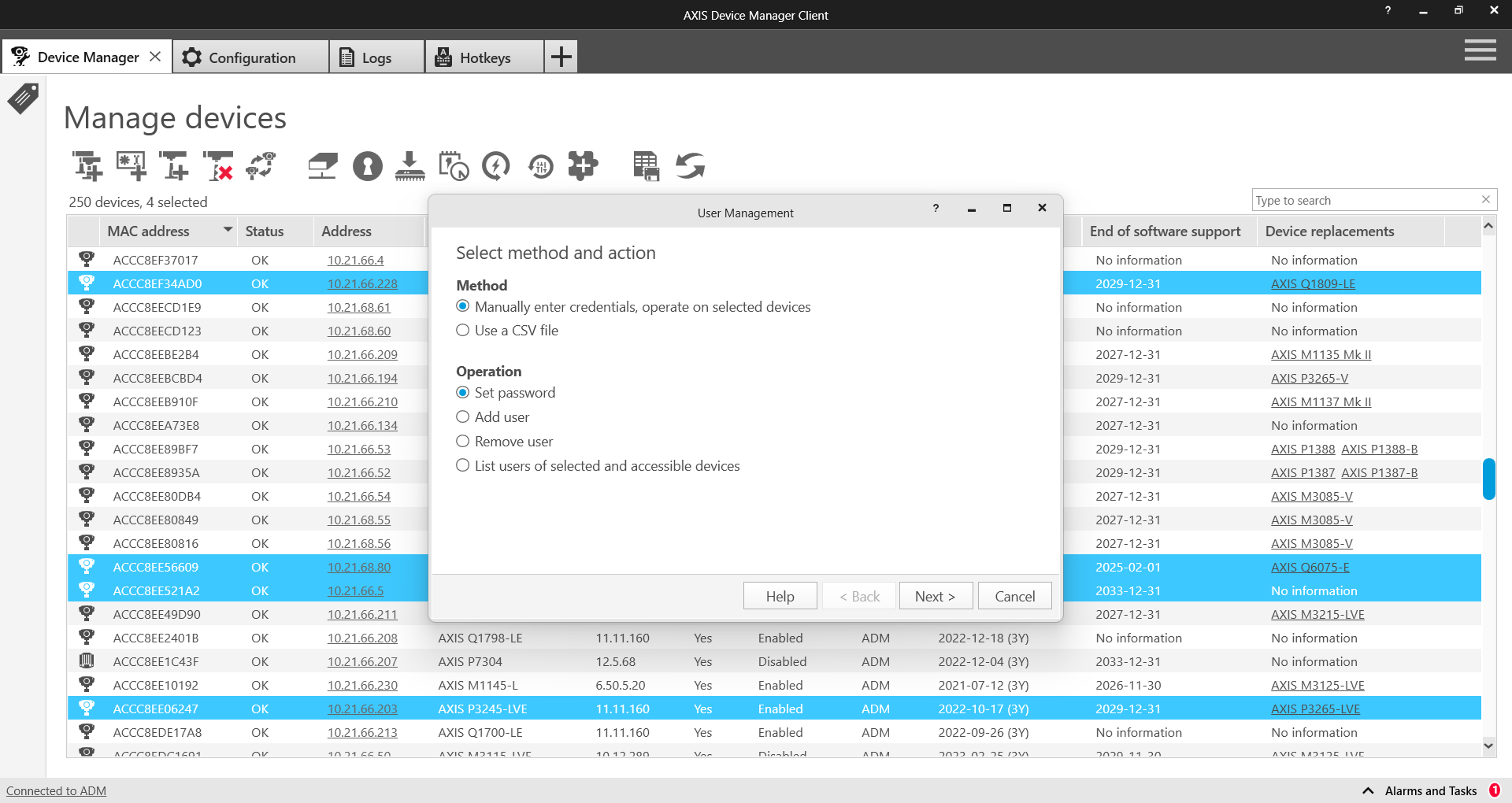
L'autenticazione e il controllo dei privilegi è una parte importante della protezione delle risorse di rete. Il criterio di implementazione aiuta a ridurre il rischio di uso improprio accidentale o intenzionale per un periodo di tempo. Imporre l'uso di password robuste è un compito fondamentale, ma lo è anche ridurre il rischio di password compromesse. Le password dei dispositivi spesso si diffondono all'interno di un'organizzazione e quando ciò accade si perde il controllo sugli utenti che possono accedervi. AXIS Device Manager consente di gestire facilmente più account e password per i dispositivi Axis.
Perché si deve avere più di un account utente nei dispositivi:
Controllare i livelli di privilegio per diversi tipi di utenti (macchine e persone).
Ridurre il rischio di compromettere la password root (master).
Poter reimpostare le credenziali per un tipo di utente senza influire sugli altri.
Utilizzo dei privilegi in AXIS Device Manager
I dispositivi Axis supportano più account, ognuno dei quali ha uno dei tre diversi livelli di privilegio:
Viewers (Visualizzatori): Questi utenti hanno accesso al video e ai Comandi PTZ.
Operators (Operatori): Gli utenti con diritti di operatore possono ottimizzare le impostazioni della telecamera e i profili del flusso video.
Amministratori: Gli amministratori possono gestire gli account, modificare le impostazioni di rete e controllare un numero di servizi nel dispositivo.
Ogni ruolo che accede alla telecamera deve avere un proprio account. Ad esempio, si potrebbe configurare il ruolo “Personale della sala di controllo“ con il livello di privilegio “operatore“, mentre il ruolo “Personale di pattugliamento“ potrebbe necessitare solo del livello di privilegio “visualizzatore“.
Passaggi consigliati
Prima di aggiungere le telecamere al VMS, aggiungere le telecamere ad AXIS Device Manager.
In AXIS Device Manager, selezionare tutte le telecamere e creare un nuovo account utente chiamato “vms“ o nome simile e impostare una password complessa. I privilegi devono essere allineati con i requisiti del VMS - che potrebbero essere l'operatore o l'amministratore (verificare con il produttore).
Aggiungere i dispositivi al VMS con l'account e la password creata.
Tornare ad AXIS Device Manager - selezionare nuovamente tutte le telecamere e reimpostare (modificare) la password dell'account “root“ con una nuova password complessa. La password dell'account “root“ deve essere nota solo a un numero limitato di persone (coloro che utilizzano AXIS Device Manager).
Quando qualcuno deve utilizzare un browser Web per accedere a un dispositivo per attività di manutenzione o risoluzione dei problemi, non fornire loro la password root. Invece, utilizzare AXIS Device Manager per creare un nuovo account (temporaneo) per il dispositivo selezionato (i dispositivi selezionati) con privilegi di amministratore o operatore. Una volta completato l'intervento, utilizzare AXIS Device Manager per eliminare l'account temporaneo.
AXIS Device Manager supporta amministratori locali e utenti e gruppi di dominio. È possibile utilizzare un amministratore locale se si accede al client AXIS Device Manager solo dalla stessa macchina che ospita il server AXIS Device Manager. Si consiglia di utilizzare gli utenti di dominio se la persona che si occupa della manutenzione del sistema utilizzerà i client remoti.
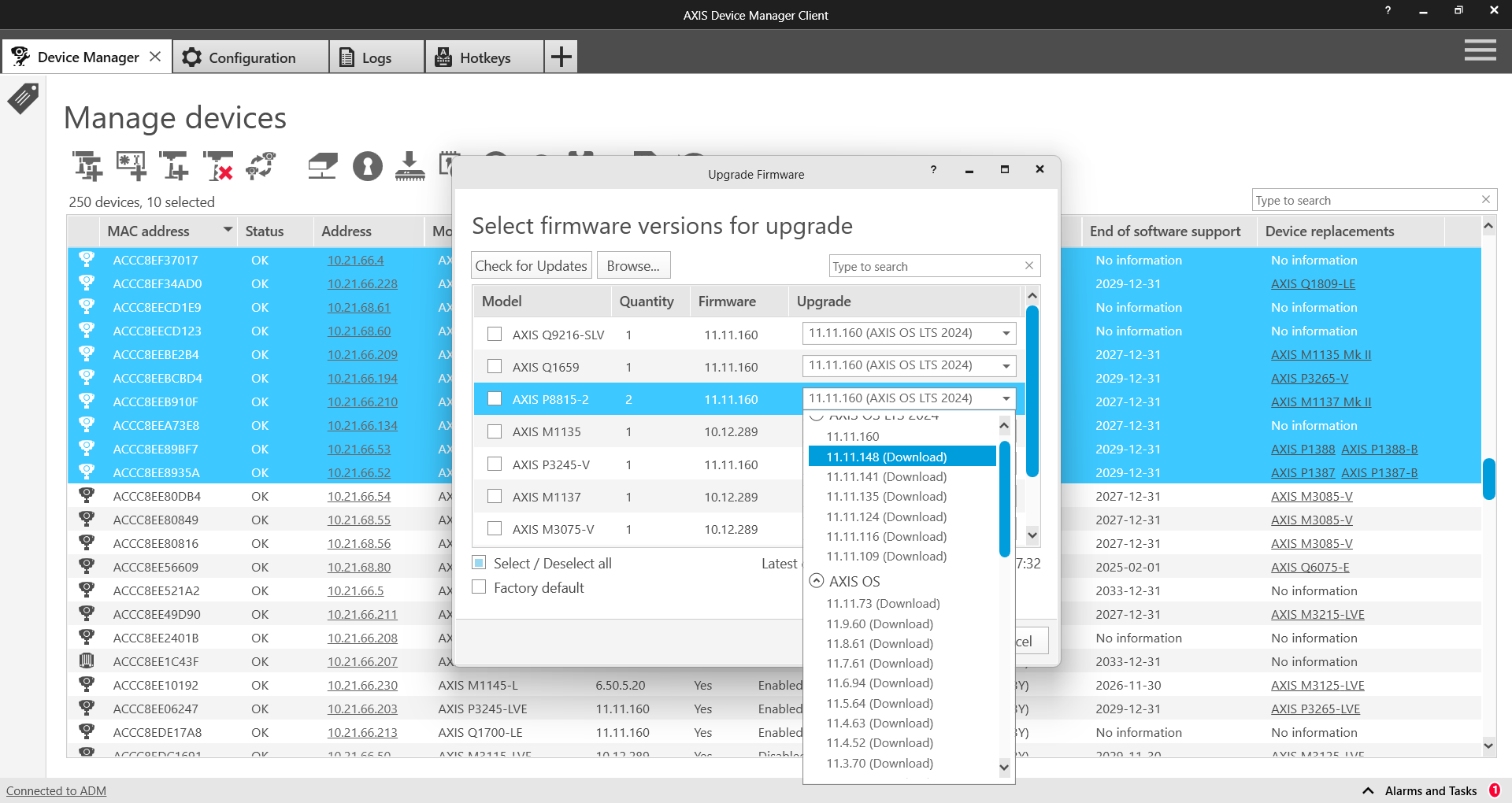
Aggiornamenti AXIS OS
Le versioni aggiornate di AXIS OS includono patch per le vulnerabilità note. È fondamentale utilizzare sempre il software più recente perché i malintenzionati potrebbero tentare di sfruttare vulnerabilità note. Altrettanto importante è la rapidità di distribuzione di una nuova versione del sistema operativo di AXIS, che aumenta le capacità operative ed elimina i rallentamenti collegati al roll-out manuale degli aggiornamenti delle nuove release. AXIS Device Manager si collega a www.axis.com e scarica le ultime versioni del sistema operativo AXIS o dei servizi applicabili. Se si preferisce non scaricare direttamente sulla rete da Internet, è possibile salvare gli aggiornamenti su una chiavetta USB e caricarli sul client AXIS Device Manager. Viene indicato anche se sono disponibili nuove versioni del sistema operativo AXIS e consente di distribuirli rapidamente sui dispositivi Axis.
Perché si devono sempre eseguire le ultime versioni del sistema operativo AXIS:
La rete e i dispositivi sono protetti con le ultime patch contro vulnerabilità note, specialmente quelle critiche.
I dispositivi vengono aggiornati con gli ultimi miglioramenti delle prestazioni e per risolvere bug e difetti.
Si ottiene accesso immediato alle ultime funzionalità e ai miglioramenti delle funzionalità.
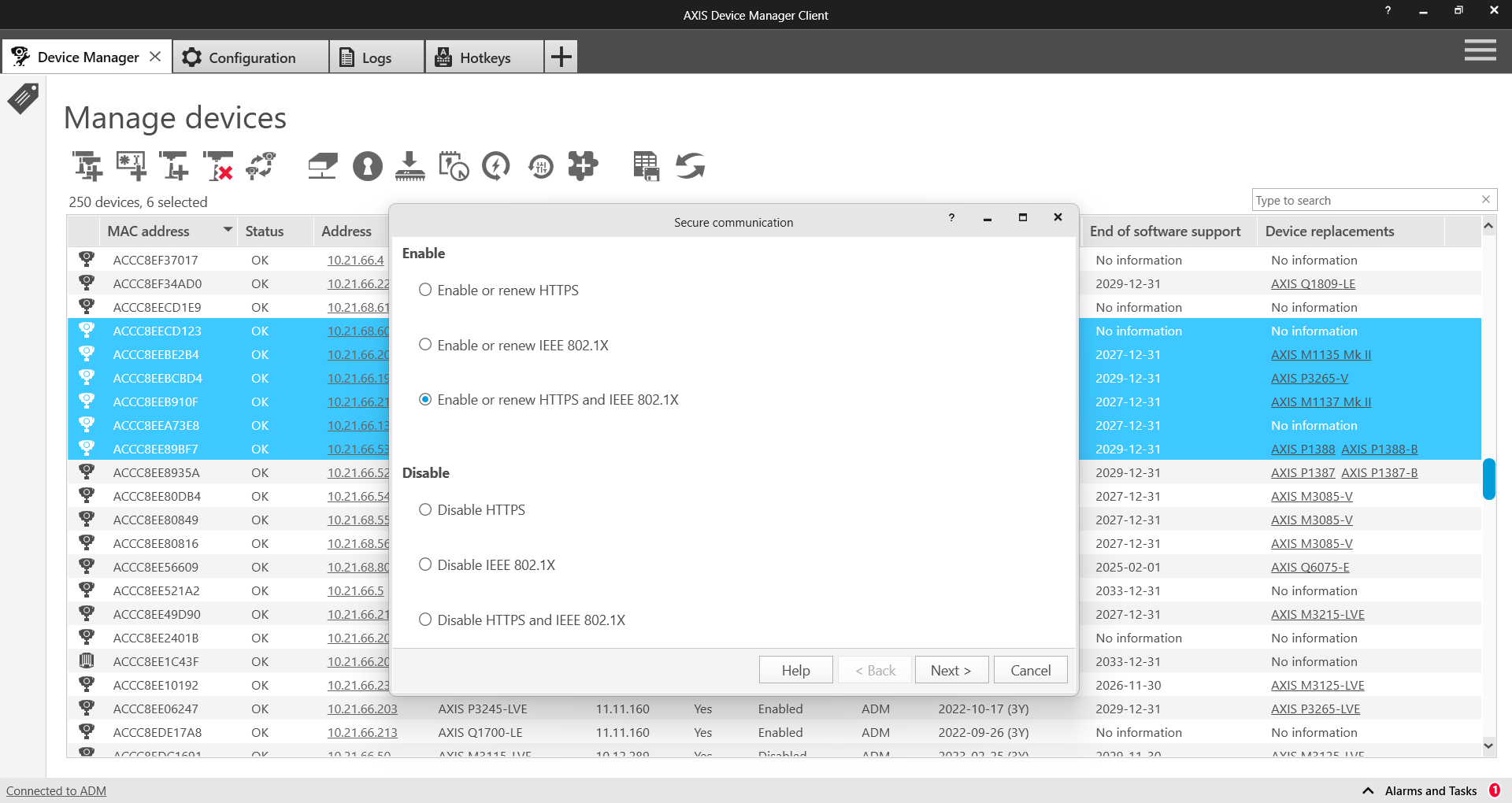
Protezione aggiuntiva
L'adozione di un buon sistema per utenti e password e l'utilizzo di versioni aggiornate del sistema operativo AXIS consentono di ridurre i rischi comuni per i dispositivi. La Guida all'hardening di AXIS descrive ulteriori misure per ridurre i rischi all'interno di organizzazioni grandi e importanti. Questo include la disattivazione di servizi che potrebbero non essere utilizzati e l'abilitazione di servizi che possono aiutare a rilevare e monitorare i segnali di un attacco o di una violazione. AXIS Device Manager semplifica il processo di distribuzione di alcuni di questi sistemi. Axis fornisce un modello di configurazione per le impostazioni raccomandate di base.
Come proteggere i dispositivi con la Guida alla protezione Axis:
Leggete la Guida all'hardening di AXIS e scaricare il file del modello alla fine del documento.
Modificare il file di configurazione per selezionare gli elementi pertinenti.
Selezionare i dispositivi nell'inventario di AXIS Device Manager.
Fare clic con il pulsante destro del mouse e selezionare “Configure Devices > Configure…“ (Configura dispositivi - Configura).
Fare clic su “File di configurazione“ e selezionare il file scaricato.
Regolare le impostazioni in base alle esigenze.
Servizio di autorità di certificazione
A Autorità di certificazione (CA) è un servizio che rilascia certificati digitali a server, client o utenti. Una CA può essere pubblica o privata. Le CA pubbliche attendibili, come Comodo e Symantec (in precedenza Verisign), vengono in genere utilizzate per servizi pubblici quali siti Web pubblici ed e-mail.
Un CA privato (in genere un servizio di directory/certificato attivo) rilascia certificati per i servizi di rete interni/privati. In un sistema di gestione video, questo serve principalmente per la Crittografia HTTPS della rete e per il controllo degli accessi alla rete IEEE 802.1x. AXIS Device Manager include un servizio CA per i dispositivi Axis e può funzionare sia come CA private root che come CA intermedio privato; come parte di un'infrastruttura a chiave pubblica (PKI) aziendale.
I certificati firmati dalla CA sono utilizzati per i certificati IEEE 802.1x (client) e HTTPS (server).
HTTPS
HTTPS è la versione sicura di HTTP su cui vengono crittografate le comunicazioni tra un client e un server. I certificati autofirmati sono sufficienti per ottenere una connessione crittografata. Non vi è alcuna differenza nel livello di crittografia tra i certificati autofirmati e i certificati firmati dalla CA. La differenza è che i certificati autofirmati non proteggono dallo spoofing di rete, in cui un computer attaccante tenta di impersonare un server legittimo. I certificati firmati da CA aggiungono un punto di fiducia per i client per autenticare che stanno accedendo a un dispositivo fidato. Si noti che il client video (VMS) deve supportare la richiesta di video su HTTPS (RTP su RTSP su HTTPS) per poter crittografare il video.
IEEE 802.1X
Spesso definito semplicemente 802.1X, questo standard impedisce ai dispositivi di rete non autorizzati di accedere alla rete locale. Un dispositivo deve autenticarsi prima di poter accedere alla rete (e alle sue risorse). È possibile utilizzare diversi metodi di autenticazione: indirizzo MAC (filtraggio MAC), utente/password o certificato client. Il proprietario del sistema decide quale metodo usare e la scelta appropriata dipende da minacce, rischi e costi.
La gestione di un'infrastruttura 802.1X è un investimento. Richiede switch gestiti e server aggiuntivi, in genere un RADIUS (servizio utente di accesso remoto per l'autenticazione remota). L'utilizzo dei certificati client richiede una CA (privata o pubblica) in grado di rilasciare certificati client. Nella maggior parte dei casi l'infrastruttura ha bisogno di personale per gestirla e monitorarla.
Gestione del ciclo di vita dei certificati
La gestione del ciclo di vita dei certificati è un mezzo per gestire in modo efficiente dal punto di vista dei costi tutti i processi e le attività relative all'emissione, all'installazione, all'ispezione, alla correzione e al rinnovo dei certificati nel tempo. AXIS Device Manager consente di gestire in modo efficiente i certificati permettendo agli amministratori di:
Rilasciare certificati firmati dal CA quando non sono disponibili altri CA
Gestire facilmente i certificati IEEE 802.1X
Gestire facilmente i certificati HTTPS
Controllare le date di scadenza del certificato
Rinnovare facilmente i certificati prima della scadenza
Consigli per i CA private root e intermedi
Non è consigliabile esporre i dispositivi Axis come server pubblici destinati al pubblico. Questo è il motivo per cui l'utilizzo di un CA pubblico per le risorse private non è economicamente conveniente.
Per HTTPS, il server VMS è l'unico client che deve convalidare l'accesso a una telecamera attendibile. I client operatore non accedono mai direttamente alle telecamere poiché i video in diretta e registrati sono forniti dal server VMS. In una tale situazione il valore per incorporare i certificati dei server delle telecamere in una PKI aziendale esistente è limitato.
L'uso di AXIS Device Manager come CA privata è la soluzione più conveniente. Dopo aver generato un certificato CA radice, installare il certificato AXIS Device Manager nell'archivio certificati del server VMS. Se ci sono altri client che accedono direttamente alle telecamere (per la manutenzione o la risoluzione dei problemi), installare CA root di AXIS Device Manager anche in questi client.
Per 802.1X, la telecamera necessita di un certificato client per autenticarsi su un server RADIUS. Si consiglia di chiedere all'amministratore della PKI/CA aziendale di generare un certificato CA intermedio ed esportarlo come certificato PKCS#12 (P12) che può essere installato in AXIS Device Manager.
Per assistenza nell'impostazione di un server FreeRADIUS, visitare la sezione Documenti tecnici per AXIS Device Manager
Conclusioni
La gestione e il controllo della sicurezza sono parti importanti dell'implementazione di un approccio efficace alla sicurezza informatica. Si tratta di un processo continuo che richiede il mantenimento di uno stato chiaro e l'adozione di azioni appropriate per mitigare qualsiasi potenziale minaccia che possa avere un impatto sulla rete IP. AXIS Device Manager offre uno strumento per gestire i dispositivi e aumentare la sicurezza della rete. Contattare il rappresentante Axis locale o visitare il sito www.axis.com per ulteriori informazioni o supporto.